Cybersecurity Insurance: Think You're Covered?
by Geoff Yeagley on May 28, 2015 at 9:46 AM
IT security breaches have become so commonplace in recent years that they barely seem to raise an eyebrow anymore: Target, Bank of America, I.R.S., the list goes on. With that rise, the claims on Cybersecurity Insurance have risen as well.
IT Auditing - Why It's a Smart Investment
by Geoff Yeagley on May 21, 2015 at 8:58 AM
We have all heard the term "Audit" and most of the time it makes us cringe. The first thing that we think of is someone in a suit coming into our organization and poking holes in our Technology, People and Processes that we have built based on the needs of our company and business. Ho …
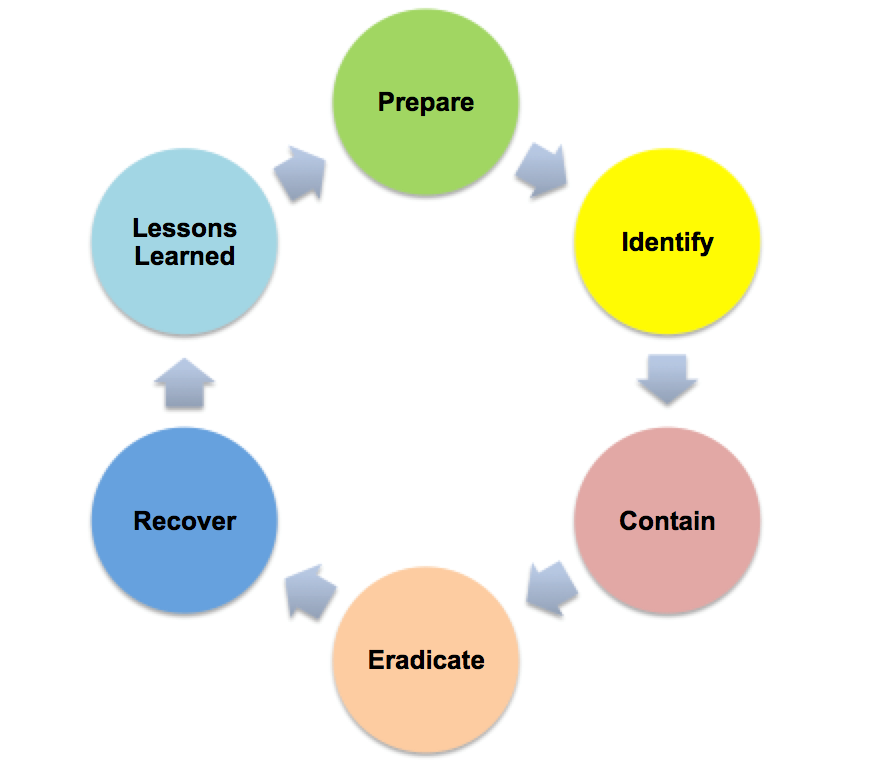
Incident Response Management: What Is It and How to Implement It
by Geoff Yeagley on May 19, 2015 at 9:20 AM
An Incident Response Program is an aggregate of processes designed to minimize the impact of security incidents. The program is like a fire extinguisher case on the wall in a high school chemistry lab. It contains all of the components, including detailed instructions, for how to cont …
Your PCI Risk Assessment: Security vs. Compliance
by Geoff Yeagley on May 14, 2015 at 8:58 AM
Most people often think that security and compliance are the same thing, especially when looking at conducting a PCI Risk Assessment. Truth is, these are two very different topics yet are interchanged very frequently. A good place for us to start is to define these terms so that we kn …
Vendor Management Software: Why You Need It Now
by Geoff Yeagley on May 12, 2015 at 8:56 AM
Vendor Management is certainly not a new topic to discuss but it certainly has been gaining quite a bit of attention lately due to some high profile new articles, namely the Target breach of 2013. In that instance, hackers gained access to Target’s point-of-sale systems to steal the c …
The PCI Risk Assessment: Three Examples of When to Conduct One
by Geoff Yeagley on May 4, 2015 at 10:19 AM
Almost every day we hear in the news more details about a suspected credit card breach that puts the personal information of thousands, if not millions, of people in the hands of individuals whose only intent is to cause them harm. Naturally this raises the question of what is a PCI R …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)