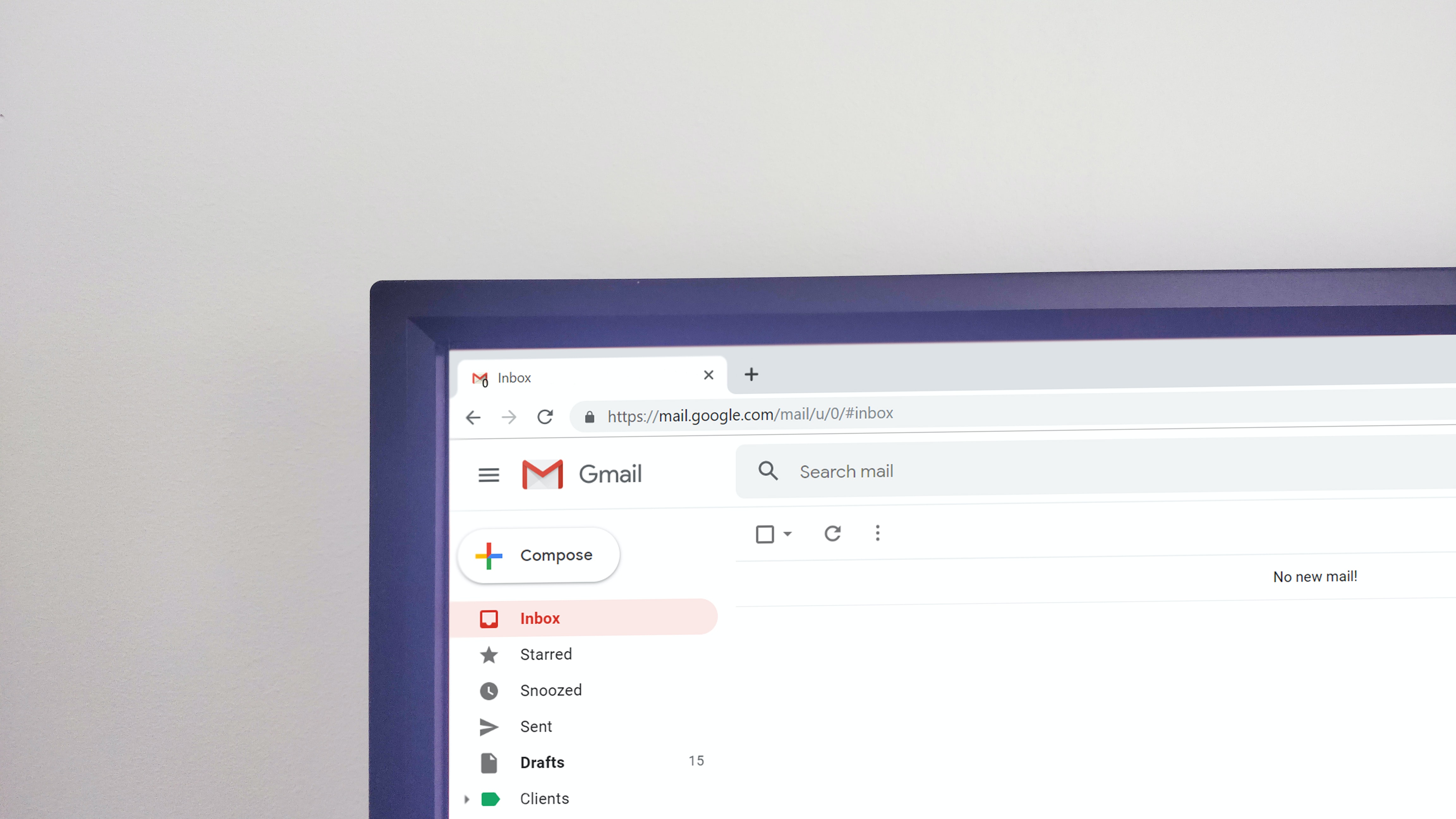
What Are DKIM, SPF, & DMARC? Why Are They So Important?
by David Bienkiewicz on June 5, 2020 at 3:30 PM
If you are asking yourself, "what is DKIM, DMARC, and SPF", you have come to the right place. DKIM, SPF, and DMARC are all email authentication technologies that are free to use for your organization. These technologies can be very useful for your organization and for domains out in t …
Examples of Effective Vishing Attacks
by David Bienkiewicz on March 4, 2020 at 2:00 PM
Vishing (not to be confused with phishing) is a form of social engineering that attempts to manipulate an individual to give an attacker personal information like usernames and passwords, credit card information, and social security numbers via the telephone. The attacker will call an …
What You Can Do to Better Prepare Yourself for Holiday Scams
by David Bienkiewicz on November 27, 2019 at 1:29 PM
It’s that time of the year again! With the holiday season upon us, many criminals will be attempting to scam people via phishing emails. This time of the year (Black Friday, Christmas) is the most lucrative for attackers due to the fact that stores are having a crazy amount of sales w …
Spear Phishing: Targeted Attacks with Higher Success Rates
by David Bienkiewicz on August 8, 2019 at 1:48 PM
Spear phishing is a deadly form of targeted social engineering. The main difference between spear phishing and traditional phishing is that spear phishing targets a certain user or users by using important facets of their life against them, while traditional phishing targets a broad g …
Trends and Tactics in Phishing
by David Bienkiewicz on May 1, 2019 at 1:00 PM
When I’m tasked with creating phishing emails for clients, I begin by looking up what the recent phishing trends are in the real world, or the top 10 most reported phishing attacks for the month / year. I often end up finding scams about winning the latest iPhone from a phone service …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)