What is Social Engineering? The Phishing Email
by Derek Morris on April 4, 2017 at 9:30 AM
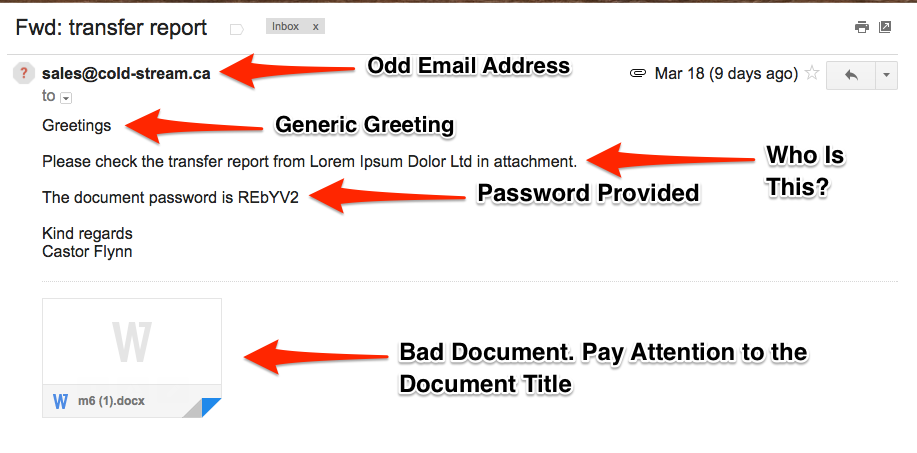
What is Social Engineering? Part 2 The seemingly most common way for an attacker to use social engineering to gain entry, exfiltrate information or disrupt business is through email phishing. As I mentioned in the previous blog, slick tactics like using nicknames and shockingly proper …
PCI Compliance Requirements: Some Tools to Help With Requirement 10!
by Derek Morris on March 29, 2017 at 10:00 AM
PCI Requirement 10 states: Track and monitor all access to network resources and cardholder data Logging mechanisms and the ability to track user activities are critical in preventing, detecting and minimizing the impact of a data compromise. The presence of logs in all environments a …
What is Social Engineering? Part I
by Derek Morris on March 14, 2017 at 9:45 AM
This post will be the first part in a series of three blog posts that outlines some of the most common methods “hackers” use, from a very high level, to gain access to your systems though social engineering tactics. The next two posts will dig a bit deeper into the different methods, …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)