What is the NIST Cybersecurity Framework?
by Geoff Yeagley on June 15, 2017 at 11:33 AM
One of the most common questions that we get here at Compass is “What is an IT Security Framework?” This is a great question as folks sometimes confuse the various frameworks with different compliance requirements or regulations that they must adhere to based on their business. If you …
Social Engineering Techniques, the Stealth Bomber, and You!
by Geoff Yeagley on May 2, 2017 at 9:45 AM
We write a lot on this blog about the different Social Engineering Techniques that are being used by bad actors today. We do this to educate you on the threats that are out there and the methods that these organizations will use to achieve their main goal: Steal sensitive information …
Why Your Information Security Program Must Evolve...NOW!
by Geoff Yeagley on April 12, 2017 at 10:39 AM
Note: For the purposes of this blog post, we are going to be looking at breach data for the United States only in 2016 2016 was a record year when it comes to data breaches, according to the Identity Theft Resource Center. According to the center, there were a total of 1,093 breaches …
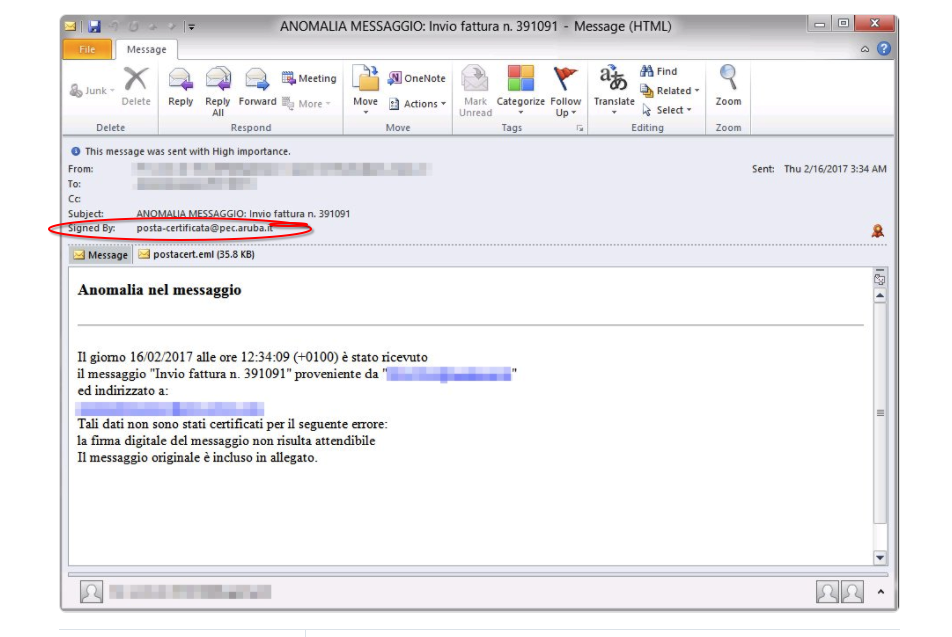
Phishing Examples - Protect Yourself From Ransomware
by Geoff Yeagley on March 8, 2017 at 10:38 AM
Fact: Phishing is the number one strategy that bad actors use to deliver malware to your organization. Fact: Phishing attacks come in a few different forms, known as phishing attacks and spear-phishing attacks. Fact: Ransomware is the most prevalent and dangerous form of Malware out t …
HIPAA Compliance and Audit Controls - What You Need to Know
by Geoff Yeagley on February 22, 2017 at 4:45 AM
If you have read the news lately on healthcare and specifically HIPAA, you probably saw references to a recent HIPAA settlement between Memorial Health Systems of Florida and the Department of Health and Human Services (HHS). I’m sure the amount of the settlement caught your attention …
The Key to Vendor Management: Truly Knowing Your Vendors!
by Geoff Yeagley on February 9, 2017 at 10:05 AM
In today's business climate, using vendors or third-party service providers is no longer a luxury, it has become a necessity. Organizations "outsource" key business functions every day for many reasons, some of which include:
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)