Cyber Safe Scholars: Developing IT Security Awareness Among Students
by Peter Fellini on April 17, 2024 at 10:15 AM
In the rapidly transforming internet era, the significance of cybersecurity emerges as a cornerstone for navigating the online world safely and responsibly, particularly for the younger generation, who are increasingly immersed in online environments. This necessity transcends the rea …
Multi-Factor Authorization (MFA) During Cellular Network Outage
by Peter Fellini on February 28, 2024 at 4:15 PM
Multi-factor authentication (MFA) stands as a crucial safeguard in thwarting unauthorized access to accounts. Traditionally, one of the most widespread practices has been the use of a mobile device as a key component in this security measure. Users typically receive a one-time passwor …
Can Neuralink Be Hacked? Cybersecurity Experts Weigh-In
by Peter Fellini on February 7, 2024 at 4:30 PM
Last month, Elon Musk, the renowned entrepreneur, revealed that his venture, Neuralink, has successfully implanted its brain-computer interface in a human subject for the first time. Musk shared on X (previously known as Twitter) that the individual is recovering well and early outcom …
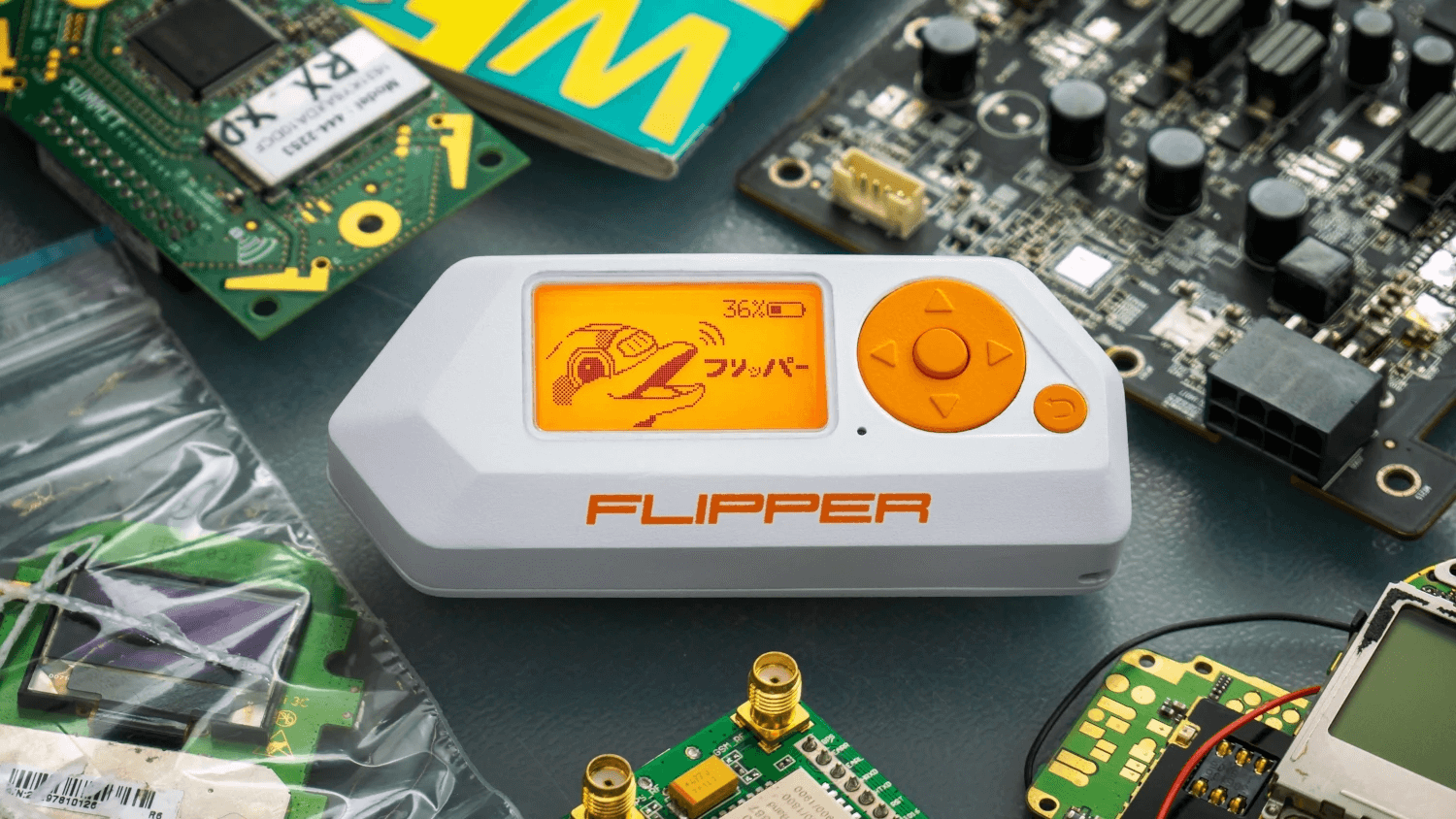
What is Flipper Zero? Portable Hacking “Multi-Tool” Explained
by Peter Fellini on August 24, 2023 at 1:00 PM
Wireless communication is integral to the modern world. Whether it is phones, Wi-Fi connectivity, or bank cards, these devices employ different types / wavelengths of wireless signals for their operations. Though infiltrating these signals traditionally demands a deep understanding of …
A Comprehensive Guide to Data Center Outsourcing (DCO)
by Peter Fellini on July 27, 2023 at 1:00 PM
Outsourcing data storage to third-party providers is a trend gaining significant momentum across organizations worldwide. Adopting this strategy brings a plethora of benefits, including significant monetary savings, improved flexibility, and a notable decrease in operational responsib …
Password Complexity – Going Beyond the Minimum Requirements
by Peter Fellini on February 23, 2022 at 1:00 PM
As the frequency and scale of cyberattacks has risen sharply over the past decade, we as end users have been repeatedly asked (and often required) to increase the complexity of our passwords. Back when the internet was in its infancy, the idea of creating a complex and tough-to-guess …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)