CIS Critical Security Controls V7.1 - What's New?
The Center for Internet Security (CIS) is a non-profit information technology entity with a mission to safeguard organizations from cyber threats. CIS has created what’s known as the CIS Top 20 Controls. These are the global standard best practices for securing information technology systems. The CIS Top 20 Controls are constantly being monitored and modified to keep up with new ongoing threats.
Changes from V7 to V7.1
CIS has taken their already heavily used best practices and made enhancements to them with the release of CIS Controls Version 7.1. Most notably they’ve added what they call “Implementation Groups” to the controls. The purpose of adding these groups is to help organizations classify themselves so they can better prioritize their efforts to make their security environment more effective.
These changes greatly benefit organizations for several reasons. The first is cost savings. Organizations can more effectively budget out their security program by figuring out which controls they should prioritize based on which one of these new implementation groups they fall under. When we see organizations struggling to maintain an effective security program, it’s often not due to lack of initiative, but more so due to lack of financial resources, and not always allocating those resources to the appropriate places. With the introduction of implementation groups, organizations can clearly understand which group they fall under, and which controls they should use their financial resources to secure first. Additionally, this greatly benefits smaller organizations that may not have the expertise or IT resources to practice good security. When they see all the CIS controls it can quickly become overwhelming. Instead of starting, they might scrap the whole project before anything is in place. With this new prioritized approach, it is clear which controls should be focused on based on which implementation group an organization falls under, making it much easier on smaller organizations with limited IT resources.
We already implemented the CIS controls; does this mean we need to start over?
Absolutely not! For organizations that have already implemented a quality security program and are following the CIS Controls, not much additional work needs to be done, if any at all. The CIS controls themselves didn’t change. The focus of adding these implementation groups was to help organizations just starting their security program to prioritize and implement the controls. My recommendation for organizations who have already been following the CIS Controls would be to look at the new implementation groups and first figure out which group you fall under. When you’ve established which group you’re in, note which controls you currently have in place corresponding to your group, and where you are lacking. This will make new security efforts going forward much less of a headache.
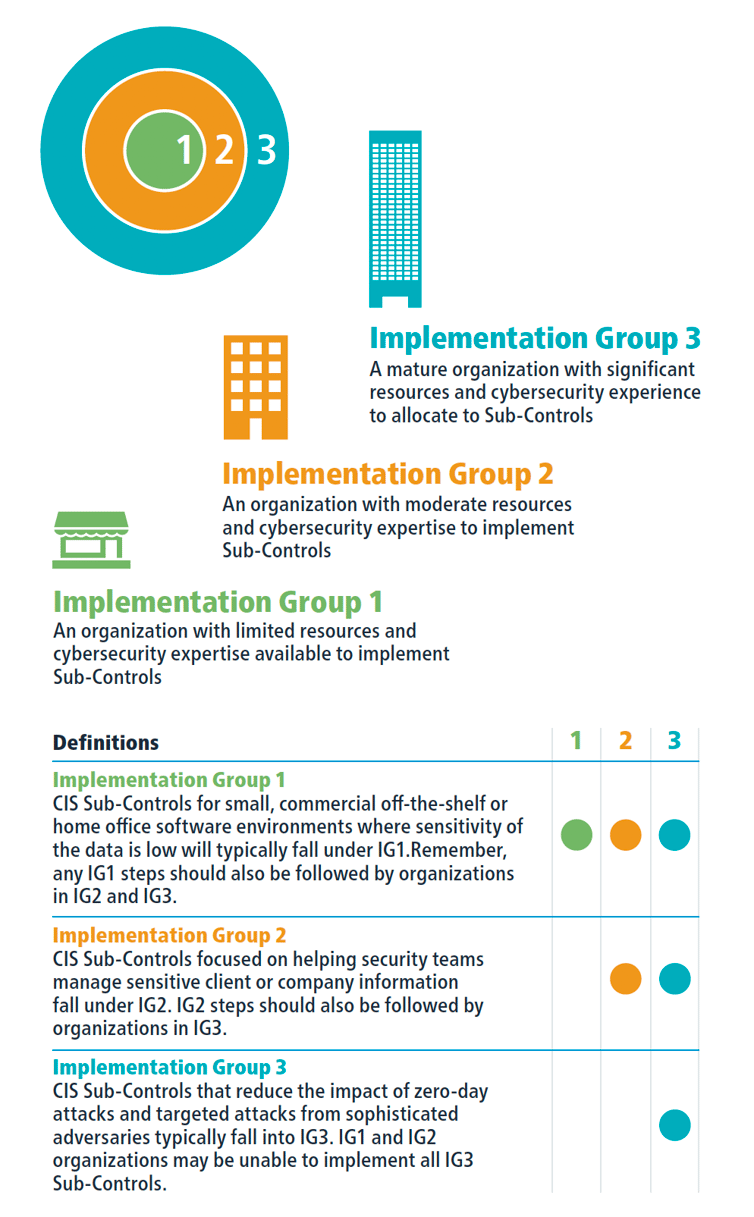
How do I know which Implementation Group I’m in?
The implementation groups are self-assessed categories based on your organization’s cybersecurity attributes. The different groups outline the sub controls, and which controls are relevant for a given group based on risk and resources. There are three different implementation groups. Each group builds upon the previous one. This means that group one will have the least amount of controls, and group three will have all the controls.
The new Implementation Groups will greatly benefit organizations by assisting in prioritizing their efforts to become secure where they previously may not have due to a lack of knowing where to begin. Compass IT Compliance offers a CIS Top 20 Critical Security Controls Risk Assessment to help organizations identify how well they align with the most current version of the CIS Controls. Contact us today to learn more about the new Implementation Groups and changes that come with the CIS Top 20 Controls V7.1!
Contact Us
Share this
You May Also Like
These Related Stories

Center for Internet Security (CIS) Controls V8 – What's New?

New Version of the Critical Security Controls Released

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think