Share this
Next story
Virtual CISO: What’s the Benefit? →
Organizations are finally beginning to implement some type of incident response plans. Most of these plans revolve around NIST 800-61 Computer Security Incident Handling Guide. This guide is an amazing framework to help your organization get something in place, however, just referencing it won’t help you in an actual incident. The publication even mentions in its abstract that although it provides guidelines for incident handling, incident handling itself is a complex undertaking.
Compass IT Compliance has started to develop incident playbooks to help our engineers during the detection and analysis phase. These playbooks are not meant to be generic, as we design them understanding that no two systems are the same. Here are some typical actions (developed by Compass IT Compliance engineers Peter Fellini and Jesse Roberts) one might take investigating a Windows host compromise.
Incident Response Compromised Windows Host – Playbook
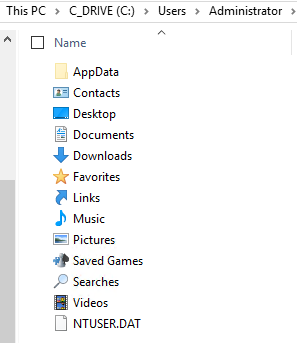
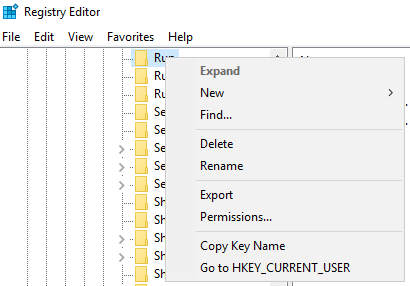
This checklist gives our engineers a good starting point in analyzing an incident. We then take the information gathered by this base checklist and use it to identify the who, what, and how of an intrusion incident. We also treat this checklist as a living document. We add to it for every similar incident we handle. Having a general incident response framework is crucial to any organization. Build upon what you know to develop playbooks so that you truly know how to respond to an incident.
For the past decade Compass IT Compliance has partnered with organizations in all sectors to assist not only in the development of incident response plans, but also in assisting in live incident response after the incident has occurred. Our incident response engineers are always available to chat should you have any questions regarding these solutions. Contact us today to learn more!
These Related Stories

No Comments Yet
Let us know what you think