Insider Threats – Your Employee May Be Your Greatest Risk
In February of 2018, Ashley Liles was working as an IT Security Analyst at an Oxford based company that suffered a ransomware attack. Ashley jumped at the opportunity, not to help the company, but to enrich himself by piggybacking on the initial ransomware attack and attempting to trick his employers into paying him the ransom instead of the original, external attacker. A few months later, the South East Regional Organized Crime Unit (SEROCU) released a press release detailing the incident.
Most ransomware attacks function in similar ways. Attackers take control of enterprise systems, whether on-premises or cloud-based, and encrypt either a portion of or all the data that the organization manages. This could be personally identifiable information (PII), confidential data, GDPR data, CCPA data, HIPAA data, PCI DSS data, etc. Once the data is encrypted, the organization is unable to access the data, or in many cases, the enterprise systems themselves. Attackers demand a ransom, typically in cryptocurrency like Bitcoin, to regain access and unencrypt the data.
While supposedly assisting with the remediation and recovery efforts, Liles actually accessed a board member’s private emails over 300 times, altered the original ransom demand email, and changed the payment address to a crypto wallet that he himself owned and controlled. He also began emailing his employers, posing as the original ransomware threat actor, and becoming increasingly threatening with demands for the ransom.
Unluckily for Liles, his employer was not interested in paying the ransom. Other IT members who were also working on the incident were able to track the fraudulent emails origination to Liles’ home IP address. Liles realized the investigators were closing in on him and wiped all data from his personal devices by the time SEROCU's cyber-crime team arrived with a search warrant, although it was still possible for them to restore incriminating data. Liles is scheduled for sentencing on July 11th. According to UK law, unauthorized computer access is punishable by up to two years in prison, while extortion carries a maximum imprisonment sentence of 14 years.
What Steps Can Organizations Take to Mitigate the Risk of Insider Threats?
Liles should not have been able to access and send emails from another employee’s email account. Access control is an essential element of security that determines who is allowed to access certain data and resources, and in what circumstances. Access control policies rely heavily on techniques like authentication and authorization, which allow organizations to explicitly verify both that users are who they say they are and that these users are granted the appropriate level of access based on context such as device, location, role, etc. Access control reduces the risk of data exfiltration by employees. Organizations both public and private must evaluate their current internal access control model to ensure employees are not able to access and download data that is not relevant to their job role.
Educate employees about cyber threats and what they can do to recognize them and prevent malicious attacks. Many industry, state, and federal guidelines/regulations require a minimum of annual security awareness education. However, in this age where the threat landscape is ever evolving, a security awareness program that includes regular reminders and updates throughout the year can keep the information fresh in the minds of employees.
Keep anti-virus and anti-malware software up to date. This is a crucial step but would not be effective against the first few attacks from recently created malware or variants to the original. A better approach is to employ behavior-based analytics protection. The use of local host-based firewalls and IDS/IPS could be used to prevent lateral movement.
Implement the principles of least-privilege to keep sensitive and confidential data separate from unauthorized users and attackers to mitigate accidental disclosures. Only system/network administrators should have administrative rights. Do not use the built-in operating system’s administrator account. System and network administrators should have a basic user account and a separate administrator account. Other system users should not have administrative rights. This will minimize their ability to install unwanted, potentially malicious applications.
Use network segmentation, access control lists, and firewalls to safeguard data and prevent unauthorized access. This may require a small investment depending on the current network switch environment, but many low-cost solutions are available today to fit any size of operation.
Patch all devices on a regular basis and maintain a well-defined patch management and vulnerability management program. Even computers that cannot access the internet need to be patched on a regular basis. Phishing has become the number one means for attackers to gain access to internal systems and insider-threats still account for more than 60% of reported data breaches.
Back up data and keep it stored in an offline location. Specific to ransomware attacks, backing up critical data can significantly reduce the impact of an incident. Armed with a timely backup and a method of restoring the operating system, a ransomware attack (excluding the exfiltration of data) would be reduced to a productivity issue related to how long it takes to get systems back into production.
Compass IT Compliance has spent the past decade helping organizations overcome these obstacles and implement robust security controls to mitigate the risk of insider threats. Contact us today to learn more and discuss your unique challenges!
Contact Us
Share this
You May Also Like
These Related Stories

Still More Ransomware
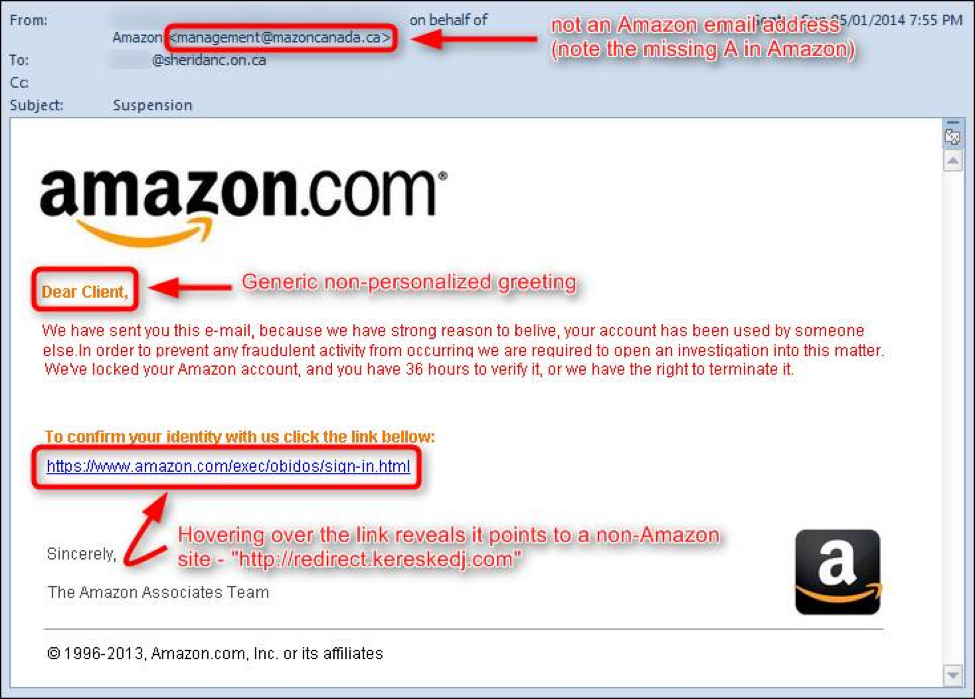
Phishing Examples: Grizzly Steppe and What You Need To Know
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
.webp?width=610&height=362&name=November%202023%20CTA%20(6).webp)
No Comments Yet
Let us know what you think