How Much Does a SOC 2 Audit Cost?
by CJ Hurd on May 7, 2024 at 1:15 PM
Navigating the financial intricacies of a SOC 2 audit requires precise planning and a deep understanding of the factors that influence its cost. From the size and complexity of your organization to the scope and depth of the audit itself, multiple elements can affect the financial res …
Privacy Concerns with Flock License Plate Recognition (LPR) Cameras
by Nicholas Foisy on May 3, 2024 at 2:25 PM
Compass IT Compliance, an expert in IT security and compliance consulting, regularly publishes blog content on data privacy topics. This article specifically addresses the growing privacy concerns associated with LPR cameras. It is important to clarify that this unbiased article was n …
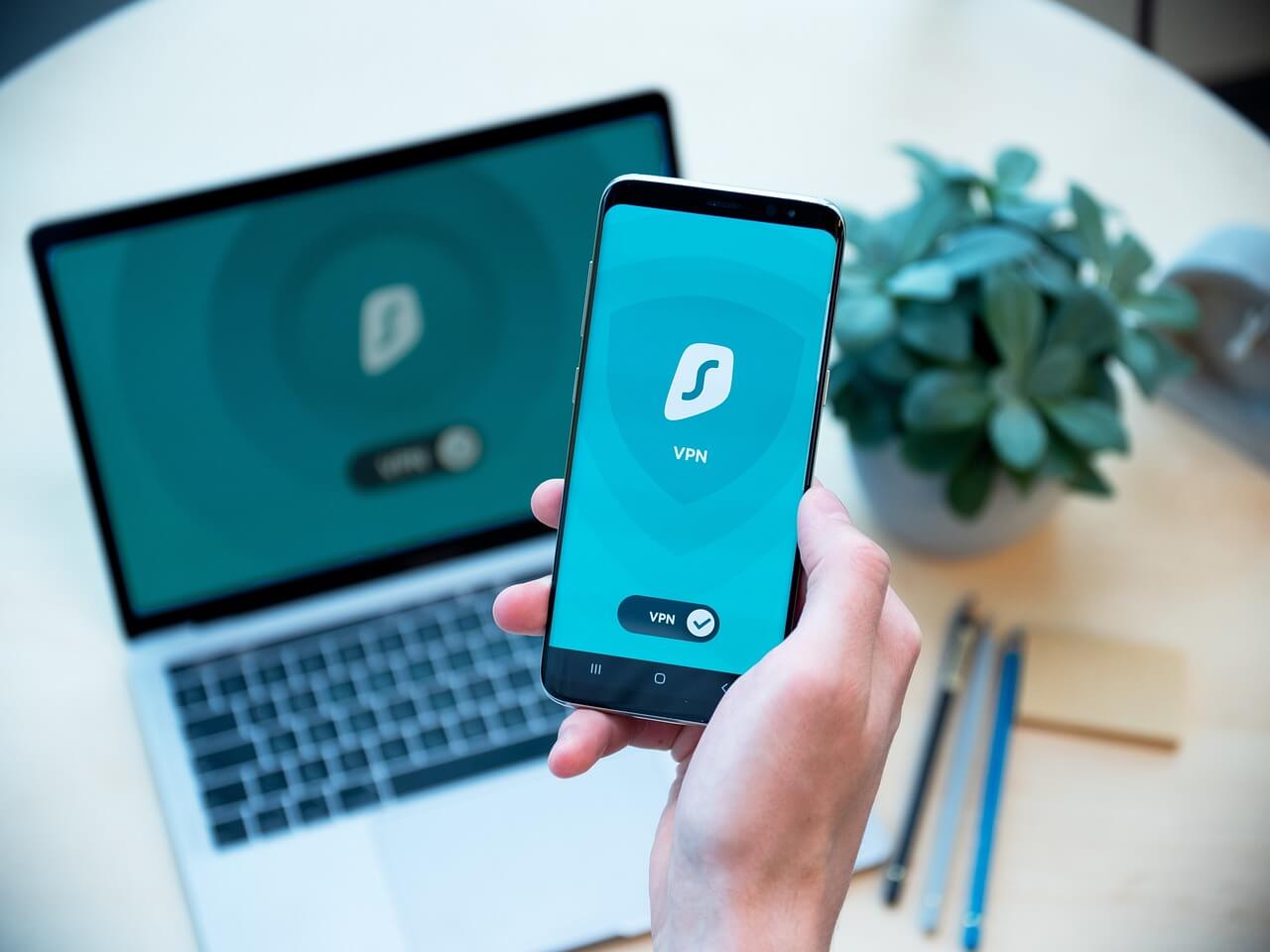
VPNs – How Effective Are They at Protecting Your Data?
by George Zapata on April 30, 2024 at 1:18 PM
As the threat of online security breaches and data privacy issues continues to escalate, virtual private networks (VPNs) have become indispensable for safeguarding sensitive information. From personal browsing habits to corporate communications, VPNs offer a layer of encryption and an …
What Is a Whaling Attack? (With Examples)
by Jeffrey Torrance on April 25, 2024 at 5:21 PM
Cybercriminals deploy a wide variety of techniques to target both individuals and organizations, aiming to extract sensitive information. With numerous social engineering strategies at play, many are curious to know, "what is whale phishing?" Whaling attacks, often referred to as CEO …
Enhancing Cloud Security Posture Management (CSPM)
by Danielle Corsa on April 19, 2024 at 12:23 PM
In recent years, the rapid adoption of cloud computing has transformed the way businesses operate. With this transformation, however, comes the pressing need to fortify cloud security. Cloud security posture management (CSPM) emerges as a vital solution, encompassing practices and too …
Guarding the Gates of Digital Identity with Image Analysis
by Adam Lyford on April 18, 2024 at 11:58 AM
Digital identities are the online essence of individuals, organizations, businesses, and beyond, serving as a gateway to global audiences and a means to connect with like-minded individuals. As the digital landscape expands, so too does the importance of robust online recognition.
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)