The Key to Vendor Management: Truly Knowing Your Vendors!
by Geoff Yeagley on February 9, 2017 at 10:05 AM
In today's business climate, using vendors or third-party service providers is no longer a luxury, it has become a necessity. Organizations "outsource" key business functions every day for many reasons, some of which include:
What is HIPAA Compliance? Just the Facts...
by Geoff Yeagley on January 24, 2017 at 10:50 AM
If you work in the healthcare industry, there is zero doubt that you have heard about HIPAA Compliance thousands and thousands of times. The importance of keeping electronic protected health information confidential is pounded into us on a daily basis and for good reason. But what is …
The PCI SAQ: Which One is Right for You?
by Geoff Yeagley on January 9, 2017 at 11:38 AM
PCI self-assessment questionnaires (SAQs) are tools that merchants and service providers must complete as evidence of their completion of the PCI DSS self-assessment. These SAQs need to be submitted yearly to your acquiring bank to demonstrate compliance with the latest version of the …
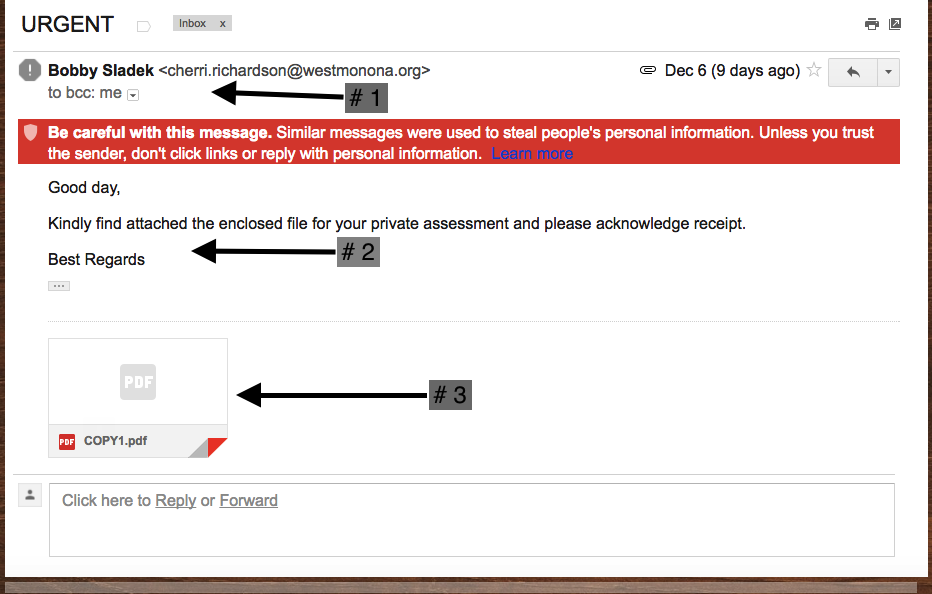
Social Engineering Techniques and How Yahoo Put Us All At Risk
by Geoff Yeagley on December 15, 2016 at 1:49 PM
I read this article the other day that one of my colleagues passed on to me that said 91% of all cyber-attacks begin with a phishing email. That is an incredible number and one that should grab your attention and the attention of your Sr. Leadership team. As you dig further into the s …
Vendor Management Requirements for Financial Institutions in New York
by Geoff Yeagley on December 12, 2016 at 9:29 AM
I recently wrote a blog post that discussed legislation in the State of New York that is set to take effect on January 1, 2017. This legislation will effect all financial institutions in the state around Cybersecurity and the development of a formal Cybersecurity program. Click here t …
5 Quick Tips To Help With Information Security
by Geoff Yeagley on November 29, 2016 at 1:30 PM
Information Security is a moving target. Once you "think" that you have it figured out, boom, here comes another new threat to knock you back on your heels and question just how strong your Information Security program is. That's the bad news. The good news is that we are going to giv …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)