SSAE 16 SOC 2 Reports: How Are They Different From Other SOC Reports?
by Geoff Yeagley on June 22, 2016 at 10:54 AM
Fact: More and more organizations are outsourcing business functions to third party providers so they can concentrate on their core business functions, reduce headcount, and ultimately save money. A great example of this is what is called Business Process Outsourcing (BPO) where compa …
3 Reasons Why You Need a HIPAA Risk Assessment Right Now
by Geoff Yeagley on June 16, 2016 at 10:31 AM
HIPAA is in the news all the time. Whether it is the tragedy that struck Orlando last weekend, the news of the HIPAA Audits coming, or a new healthcare breach being reported, we are constantly bombarded with why HIPAA compliance is critical. As with any organization, protecting and sa …
The State of Security: Healthcare Security and a HIPAA Audit
by Geoff Yeagley on June 13, 2016 at 11:26 AM
Healthcare Security, particularly IT Security, is dominating the news cycles recently, for a number of reasons. The primary reason, however, is that the healthcare sector continues to be a prime target for hackers, organized crime entities, and nation states due to the significant amo …
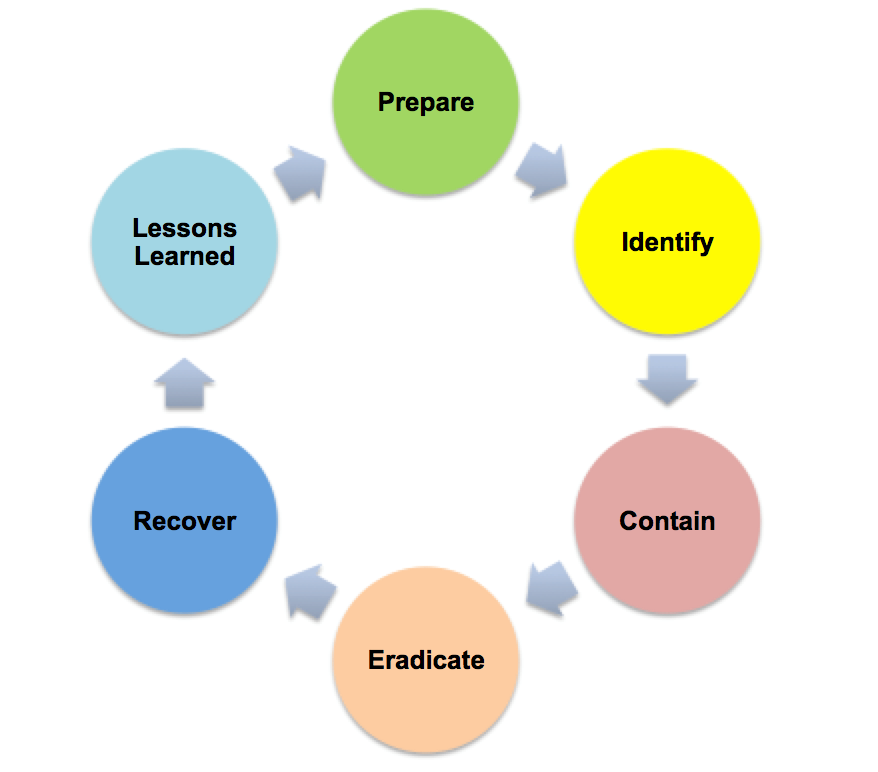
Why You Need an Incident Response Plan Now!
by Geoff Yeagley on June 7, 2016 at 10:43 AM
Two weeks ago, Compass IT Compliance had the opportunity to attend and present at the Card Not Present Conference in Orlando. This conference focuses on working with organizations that accept credit and debit cards either online, over the phone, or any other way where the credit or de …
Critical Security Control 19: The Incident Response Plan
by Geoff Yeagley on May 17, 2016 at 12:16 PM
In the world of Information Security, we have all heard of the Center for Internet Security Top 20 Critical Security Controls (CSC's) which is formerly known as the SANS Top 20. This is a list of the 20 IT Security Controls that an organization can implement to strengthen their IT Sec …
Don't Let Ransomware Take Your Money: Use an Incident Response Plan!
by Geoff Yeagley on May 12, 2016 at 11:06 AM
I feel like all I have been writing about for the past month has been Ransomware. Obviously that is due to the fact that Ransomware is in the news all the time, every day, with new trends that are happening, new "victims" that are identified, and how these organized crime entities kee …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)