Information Security Programs: Where to Start?
by Geoff Yeagley on March 15, 2016 at 10:00 AM
Hack, breach, phishing, spear phishing, ransomware. These are all words that we hear in the news on a daily basis due to some sort of threat that exists in the world of technology and information security. Most organizations have compliance requirements that they must adhere to, wheth …
The HIPAA Risk Assessment - Who Needs One and When?
by Geoff Yeagley on March 9, 2016 at 10:30 AM
Healthcare breaches are nothing new, in fact they have become quite common in the news on a weekly basis. As an example of this, a Central Florida Oncology provider recently announced that it suffered a data breach at the hands of a hacker, resulting in the compromise of the personal …
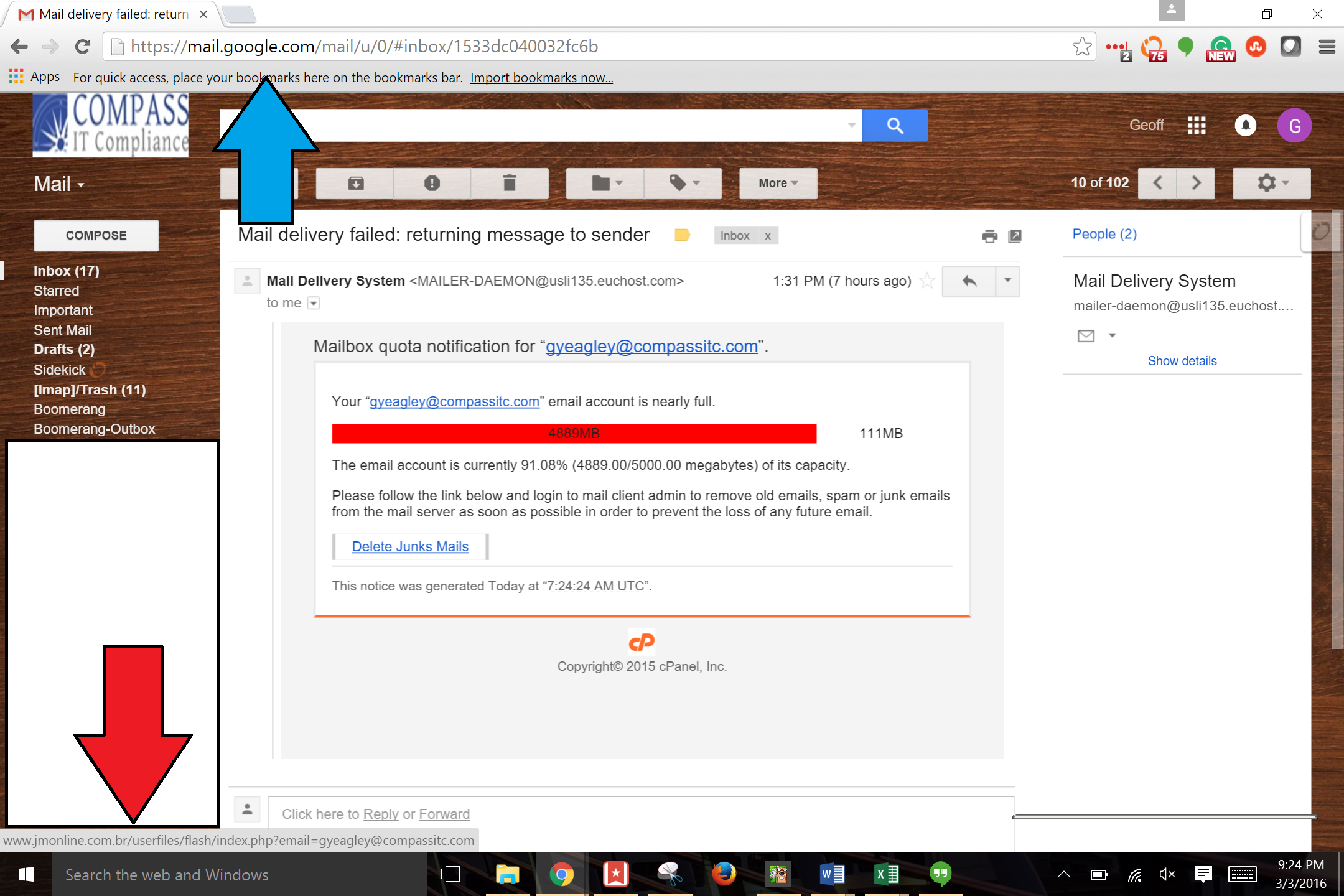
Phishing Examples: Even the Security Folks Get Targeted
by Geoff Yeagley on March 4, 2016 at 10:00 AM
We all hear about phishing emails. All the time. In fact, there is a never ending dialogue about phishing emails in the news, the most recent one being the IRS emailing to say that you owe them money and they are going to arrest you if you don't pay immediately. As a side note, this i …
How are Star Wars and the Numbers 1-6 Related?
by Geoff Yeagley on March 1, 2016 at 12:11 PM
If you guessed that they are some of the worst passwords used in 2015, you would be correct! The 2015 annual list of the worst passwords used by individuals was released and coming in at #1 again this year is "123456". Coming in at #2 was everyone's favorite: "password". The shame of …
IT Risk Assessment and the SANS Top 20 - Part IV
by Geoff Yeagley on February 23, 2016 at 11:00 AM
I know, I know. Before you even say it, they are called the Center for Internet Security Critical Security Controls, not the SANS Top 20 anymore. But, everyone knows them as the SANS Top 20 and often times still refers to them by this name which is why I stuck with it for the final pa …
SSAE 16 SOC 2 Reports: What Are They?
by Geoff Yeagley on February 18, 2016 at 12:28 PM
The SSAE 16 process, on the surface, sounds confusing. Most of this has to do with the terminology that is used, particularly the similarity of the terms used. In this blog post we are going to cover what the SSAE 16 is, what the different SOC Reports, what are the different types of …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)