What is Social Engineering? Part III
by Derek Morris on April 11, 2017 at 10:00 AM
What is Social Engineering? In this blog, I would like to shed some light on some other types of social engineering and provide some context on how to protect your business and self. In my first two blogs, I jumped into the Phishing and Spear Phishing pieces of a social engineering at …
What is PCI Compliance?
by Kyle Daun on April 6, 2017 at 10:00 AM
What is PCI Compliance? The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that regardless of size or number of transactions, any business that accepts, processes, stores or transmits credit card information maintains a secure …
What is Social Engineering? The Phishing Email
by Derek Morris on April 4, 2017 at 9:30 AM
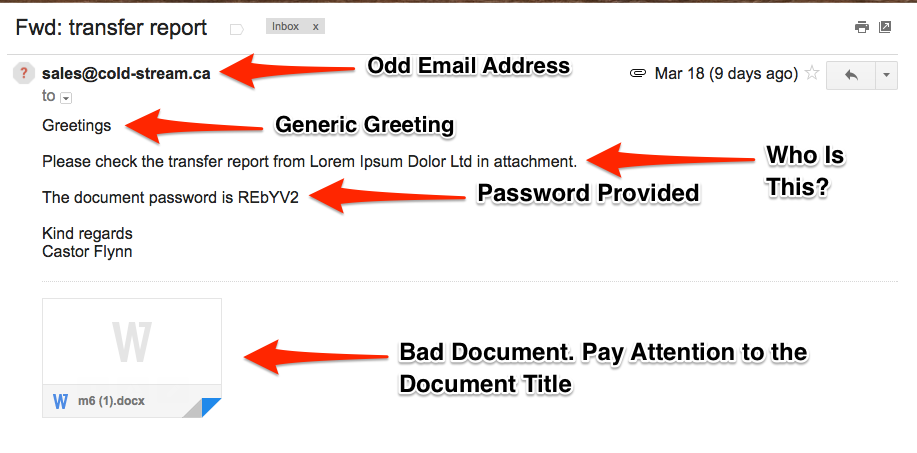
What is Social Engineering? Part 2 The seemingly most common way for an attacker to use social engineering to gain entry, exfiltrate information or disrupt business is through email phishing. As I mentioned in the previous blog, slick tactics like using nicknames and shockingly proper …
PCI Compliance Requirements: Some Tools to Help With Requirement 10!
by Derek Morris on March 29, 2017 at 10:00 AM
PCI Requirement 10 states: Track and monitor all access to network resources and cardholder data Logging mechanisms and the ability to track user activities are critical in preventing, detecting and minimizing the impact of a data compromise. The presence of logs in all environments a …
HIPAA Compliance: 5 HIPAA Mistakes to Avoid!
by Derek Boczenowski on March 28, 2017 at 9:30 AM
Here at Compass, we have seen a huge upswing in the number of HIPAA / HITECH risk assessments we have been conducting over the last year. Covered entities (Doctors, Hospitals, Pharmacies) and health plans are obviously storing PHI (protected health information) and ePHI (electronic pr …
Why You Need an Incident Response Plan....Now!
by TJ Quirk on March 21, 2017 at 10:00 AM
You’ve been breached. Now what? New vulnerabilities are coming fast and furious. The unfortunate truth for most of us is, it’s not a matter of IF we are breached, it’s a matter of WHEN we are breached. Replace the worry with a plan - an Incident Response Plan. What qualifies as an inc …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)