Phishing Examples: Grizzly Steppe and What You Need To Know
Within the past few years, Russian hacking has become a major issue in the United States. Not only has Russian Intelligence targeted political campaigns, they have also taken interest in other types of organizations who hold critical information. The Russians have developed a method of hacking that ultimately allows them unauthorized access into systems with the goal to exfiltrate information. The Department of Homeland Security thus named this dangerous Russian cyber activity “Grizzly Steppe”.
Phishing emails are one of the most common hacking methods used today. Whether they are used to gain unauthorized access to a system or to obtain user credentials, they are still proving to be rather effective for hackers. Foreign attackers have also been taking advantage of such a simple way of gaining information. Russian Intelligence has been using this hacking technique for years on government organizations, critical infrastructure entities, think tanks, universities, political organizations, and corporations. Phishing examples might include something like the email below:
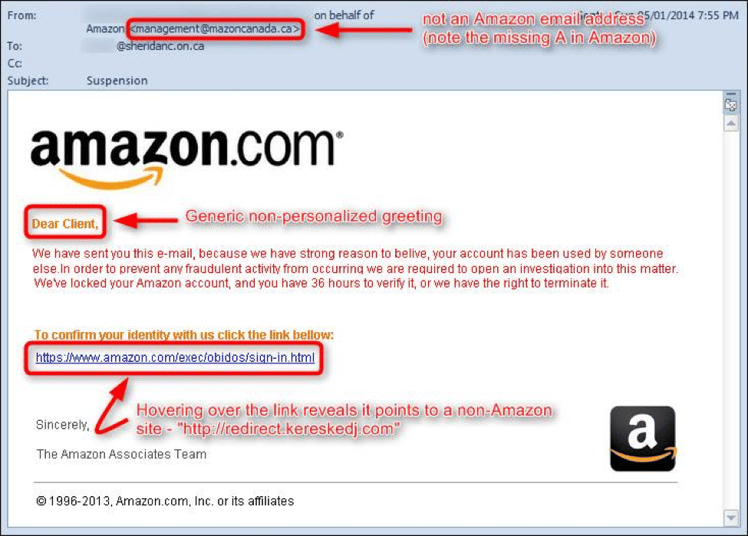
This phishing scam is mimicking amazon.com, a popular, trusted company. This is just an example of how attackers can make sophisticated looking emails that the user may not think twice about. With the proper examination and knowledge of these types of attacks, falling victim can be avoided.
Grizzly Steppe Cyber Threats
Two cyber threats that attacked a U.S. political party have been detected, APT29 and APT28 (Advanced Persistent Threat). These groups attacked the same U.S. political party approximately a year apart; APT29 in the summer of 2015 and APT28 in the spring of 2016.
APT29 used spear phishing attacks to gain unauthorized access to targeted systems. Once in these systems, the hackers extracted sensitive information back to their source location.
APT28, the most recent attack, created fraudulent email addresses to trick users of a U.S. political party into entering personal credentials into a malicious site. This attack used a spear phishing campaign that mimicked a trusted user’s email address. The email contained a link to a malicious site that requested a change to the user’s password. When the user clicked into the malicious site, their credentials were harvested. The harvested credentials were then used to steal information from the targeted systems.
Cybersecurity Best Practices
The following best practices can help lessen the chance of cyber-threats gaining access to your organization’s systems. Employee training on best practices in cyber security is crucial due to a substantial number of hackers using email phishing tactics. While it is sometimes difficult to distinguish a phishing email from a legitimate one, employee training can at least reduce the chances of falling victim. Businesses should also make sure the following are currently in effect for their organization:
- Regular backups should be taken and stored offline
- Run cybersecurity risk analysis
- Train staff on cyber threats and how to avoid them
- Run vulnerability scans and patch known vulnerabilities
- Only allow approved applications to be installed
- Have an incident response plan and practice this plan
- Test if the business can run in the event a system goes down
- Have a penetration test performed on systems (internal and external)
Suggestions for Mitigating Attacks
Along with best practices, IT employees should be sure their network is secure and up to date to lessen the chances of an attack occurring. When these actions are implemented into an organization, actors such as Russian intelligence will have more difficulty gaining access to important systems. These suggestions include:
- Stay up to date with patches
- Have an application whitelisting policy
- Restrict administrative privileges
- Network segmentation & segregation
- User input validation
- Set file reputation to maximum settings
- Understand firewalls
Yara Rule
A Yara Rule is a tool that assists security experts in identifying malware samples. Another safe practice may be creating a Yara Rule to analyze an intrusion after it has happened for more information. These rules will not prevent or detect an attack, but they will allow experts to dig deeper into why an attack happened. Some coding experience may be necessary to create such a rule, as they follow the C programming language convention. Basically, this Yara rule detects a web shell tool commonly hit by Russian hackers. With one such as the example in place, more information can be gathered about an intrusion that happened:
rule PAS_TOOL_PHP_WEB_KIT
{
meta:
description = "PAS TOOL PHP WEB KIT FOUND"
strings:
$php = "<?php"
$base64decode = /\='base'\.\(\d+\*\d+\)\.'_de'\.'code'/
$strreplace = "(str_replace("
$md5 = ".substr(md5(strrev("
$gzinflate = "gzinflate"
$cookie = "_COOKIE"
$isset = "isset"
condition:
(filesize > 20KB and filesize < 22KB) and
#cookie == 2 and
#isset == 3 and
all of them
}
For our March webinar, we are going to dig into Grizzly Steppe in greater detail and discuss phising examples in greater detail and how you can protect yourself! Details and the link to register are below:
When: Thursday, March 16, 2017 @ 1:00 PM
Duration: 30-Minutes with Q&A Session
Contact Us
Share this
You May Also Like
These Related Stories
Brute Force Attacks: How To Safeguard Your Password

Phishing vs. Pharming: What's the Difference?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)

No Comments Yet
Let us know what you think