Protecting SCADA Systems from Cyber-Attacks
Supervisory control and data acquisition (SCADA) is a control system architecture comprising computers, networked data communications and graphical user interfaces (GUI) for high-level process supervisory management, while also comprising other peripheral devices like programmable logic controllers (PLC) and discrete proportional-integral-derivative (PID) controllers to interface with process plant or machinery. SCADA systems are commonly utilized in industries such as energy, oil and gas, water, power, manufacturing, and many more.
SCADA Cybersecurity
Both the scale and frequency of cyberattacks on SCADA systems has been growing recently. This past February, hackers broke into a water treatment facility in Florida, gained access to an internal ICS platform and changed chemical levels, attempting to making the water unsafe to consume. Luckily, a plant operator immediately noticed and corrected the chemical levels. This type of attack highlights the extreme consequences that cyber attacks on SCADA systems can have.
SCADA Security Best Practices
To assist organizations in enhancing their SCADA security posture, Compass IT Compliance has developed the following checklist of recommendations and best practices:
The Non-Patched Question
A significant number of SCADA systems have not had their operating system (OS) patched for a long time
- Recommend asking your SCADA vendor to clearly provide a step-by-step guidance for patching the OS underlying your system
Improve Authentication
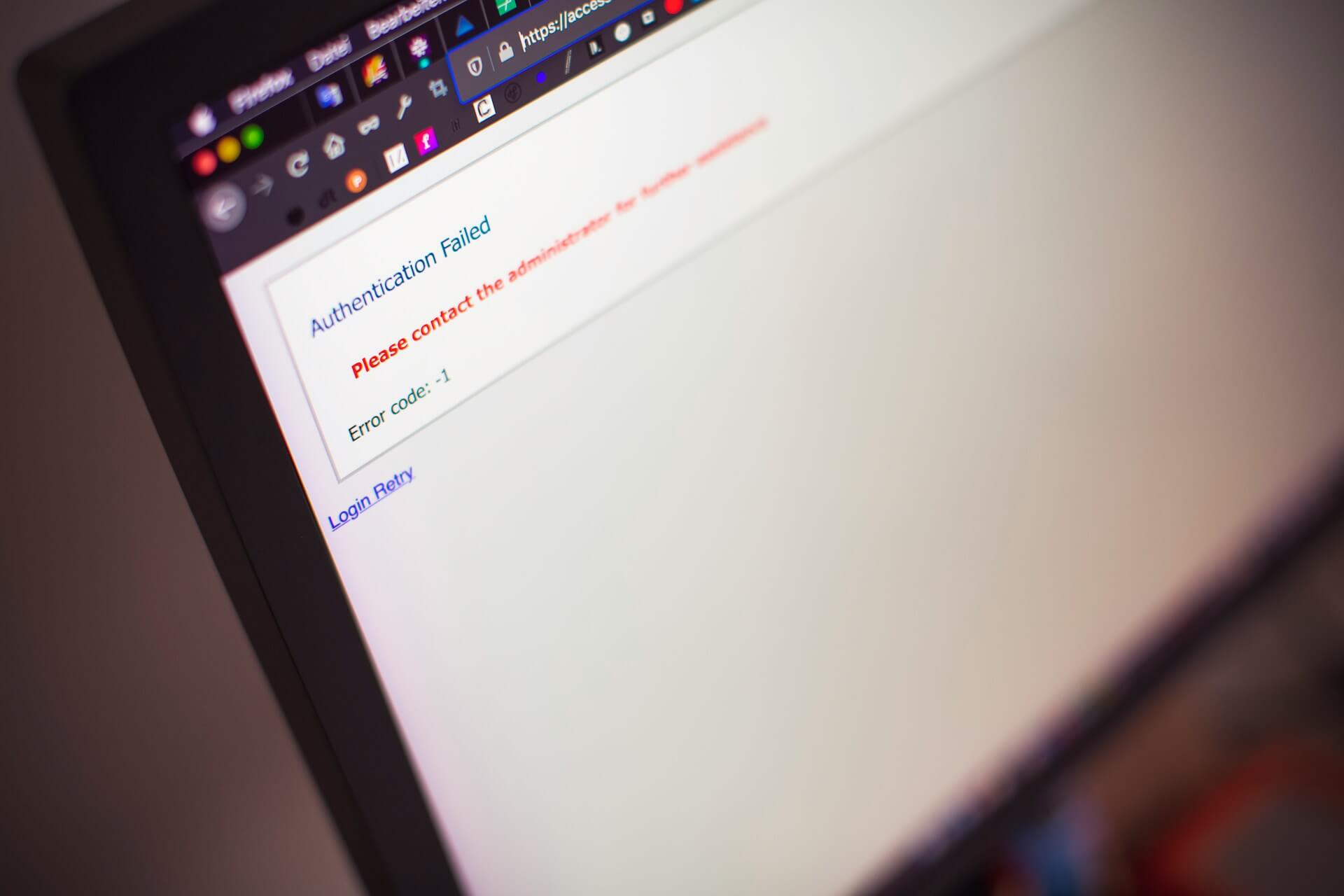
SCADA software has a very basic authentication and authorization, a malicious attacker can very easily crack it and penetrate a SCADA environment
- Recommend configuring the authentication per user and to use authorization and logging controls
- A token-based authentication can be implemented
The Data-Communication Threat
Many SCADA protocols were created before the internet era and are not adapted to the web environment
- Identify if the SCADA environment is employing the latest protocols
- Ensure that they are configured to use the new features; if upgrades are not available, evaluate if there is a way to use a secure channel for communication
Assess Remote Sites Connected to the SCADA Network
- Any location that is connected to the SCADA network is a potential target for SCADA attacks
- Conduct a physical security survey and inventory access points at each facility that has a connection to the SCADA system
Involve Top Management
Management should establish clear directions regarding its expectations in terms of SCADA cybersecurity performance within environments and interconnecting systems
Steps to Securing SCADA
- Identify all connections to SCADA networks
- Disconnect unnecessary connections to the SCADA network
- Evaluate and strengthen the security of any remaining connections to the SCADA network
- Harden SCADA networks by removing or disabling unnecessary services
- Do not rely on proprietary protocols to protect your system, implement proper authentication and authorization mechanisms
- Implement the security features provided by device and system vendors
- Establish strong controls over any medium that is used as a backdoor into the SCADA network
- Implement internal and external intrusion detection systems and establish 24-hour-a-day incident monitoring
- Perform technical audits of SCADA devices and networks, and any other connected networks, to identify security concerns
- Conduct physical security surveys and assess all remote sites connected to the SCADA network to evaluate their security
- Establish SCADA “Red Teams” to identify and evaluate possible attack scenarios
- Establish a network protection strategy based on the principle of defense-in-depth along with a risk management process
- Clearly identify cybersecurity requirements and processes employed to assess the network regularly for known vulnerabilities
- Establish effective configuration management process
- Establish system backups and disaster recovery plans
- Establish policies and conduct training to minimize the likelihood that organizational personnel will inadvertently disclose sensitive information regarding SCADA system design, operations, or security controls in place
Let Compass IT Compliance Assess Your SCADA System
Following the best practices listed above is only the first step. All organizations should be conducting some form of security assessment with a trusted third-party assessor at least annually, to have an unbiased set of eyes confirm that all risks are being mitigated as much as possible. Compass IT Compliance has spent the past decade serving as that trusted, highly certified third-party SCADA cyber security consultant for numerous organizations across the United States. Contact us today to speak with one of our security experts and discuss your unique situation!
Contact Us
Share this
You May Also Like
These Related Stories

New CJIS Requirements: What You Need to Know
Aligning Zero Trust Principles with SOC 2 Trust Service Criteria

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think