SOC 1 vs SOC 2 Reports - What's the Difference?
As the landscape of modern business shifts, one thing becomes clearer: outsourcing is not just a fleeting trend, but a strategic move adopted by companies across industries. With this increasing reliance on third-party services, there emerges an unprecedented need for more rigorous mechanisms to ensure the security and efficiency of these collaborations. Herein enters the significance of SOC reporting. This system plays a pivotal role in assuring companies that their sensitive information and financial data remains safeguarded. But to harness their full potential and remain compliant, one needs to get familiar with the nuts and bolts of SOC audits.
What is a SOC Report?
Previously called Service Organization Controls (SOC) reports, the present-day System and Organization Controls reports (distinct from the SOC that stands for security operations center) function as a way to ensure that potential vendors uphold specific industry best practices. These are not just any generic reports, but offerings created by the American Institute of Certified Public Accountants (AICPA). Engaging Certified Public Accountants (CPA) to conduct the audits, these reports focus on the system controls of service organizations, ensuring they align with the Statement on Standards for Attestation (SSAE) 18.
These best practices include guidance on finances, security, availability, confidentiality, processing integrity, and privacy. What amplifies their credibility is the involvement of independent auditors. By doing so, these reports paint an unbiased picture, offering a comprehensive assessment for those considering a partnership with the evaluated entity.
What Are the Different Types of SOC Reports?
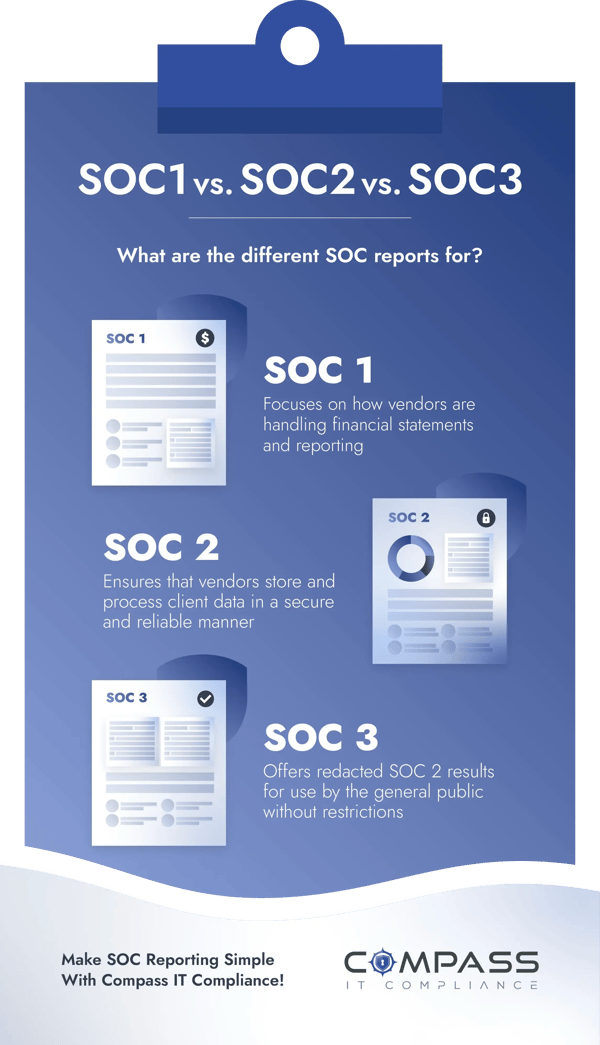
The SOC framework undergoes validation via a series of audits. Three distinct SOC report categories exist, each addressing varied facets of an organization's functions and the nature of participating organizations:
- SOC 1 – This report zeroes in on a vendor’s prowess in controlling financial reporting. It serves as an assurance to companies that their financial reporting is in safe hands when outsourced.
- SOC 2 – This report delves deep into the cybersecurity fabric of the vendor, ensuring their digital fortress is impregnable.
- SOC 3 – Although it overlaps with SOC 2 in its cybersecurity focus, SOC 3 offers a more bird’s eye perspective, less detailed compared to the comprehensive SOC 2.
What is a SOC 1 Report?
Serving as a testament to controls pertaining to client's financial report accuracy, SOC 1 reports are tailored to meet the unique needs of clients and the specialized auditors assessing their financial statements. These reports are not public documents but are instead shared exclusively among the organization's clients and the CPAs that audit the clients’ financial statements (user auditors). The necessity of such reports becomes evident when organizations rely on external entities for pivotal financial report controls. For instance, when partnering with a payroll service, certain safeguards associated with payroll processing are executed by that service. By reviewing the payroll provider's SOC 1 reports, one can ascertain the efficiency and reliability of these safeguards.
What is a SOC 2 Report?
SOC 2 stands for Systems and Organization Controls 2. This report was created by the AICPA in 2010 and is used to evaluate the potential risks linked with external software solutions that store client data online. These reports confirm that a solution offered by a service organization (like those from SaaS providers) underwent evaluation by a Certified Public Accountant (CPA) following AICPA-established standards, covering areas such as Security, Availability, Confidentiality, Processing Integrity, and Privacy. While people often term it as "SOC 2 certification," it is more appropriate to call SOC 2 an attestation. The auditors do not declare that a company has achieved the set standards, but rather, the report details their observations on the company's security measures.
The 5 Trust Service Criteria of a SOC 2 Audit
The bedrock of SOC 2 audits rests on the five Trust Services Criteria (TSC), established by the AICPA’s Assurance Services Executive Committee (ASEC). Although the Security criterion is mandatory for all SOC 2 reports, the rest are elective, allowing businesses to customize based on their unique requirements:
- Security – This stands as the cornerstone, making it a mandatory component for every assessment, often dubbed the common SOC 2 trust service criteria. It encompasses the full life cycle of data. The measures within this domain aim to thwart or spot malicious intrusions and unsanctioned leaks of confidential details.
- Availability – This centers on ensuring your systems consistently meet uptime and performance benchmarks. Elements such as monitoring network performance and strategies for disaster recovery fall within this realm. It further delves into your enterprise's approach to security incident handling. Policies around data backups, recovery, and business continuity align with this SOC 2 trust service criterion.
- Confidentiality – This highlights the protection of sensitive data throughout its existence. The criterion advocates for businesses to shield classified assets like intellectual property, financial records, and other pivotal information tailored to your contracts with clients. Achieving this requires formulating access control and appropriate privileges, ensuring data exposure is limited to sanctioned personnel or entities.
- Processing Integrity – This aspect is assessed when ensuring data in the cloud is processed accurately, reliably, and in a timely manner. It further ascertains if the systems fulfill their designated role. Utilizing robust quality assurance checks and specific SOC tools can aid in supervising data processing.
- Privacy – This criterion examines the protection of Personal Identifiable Information (PII) against potential breaches and unauthorized removal. It mandates the execution of stringent access measures, multi-factor authentication, and data encryption.
What is a SOC 3 Report?
Designed for a broader audience, SOC 3 reports cater to those who seek assurance regarding organizational controls relevant to security, availability, confidentiality, processing integrity, or privacy, but without delving into the technical details that a SOC 2 report offers. Being less granular, it skips over the nitty-gritty details of systems, controls, and testing results. As a result, these are often considered general-use reports and serve dual purposes - providing assurance and acting as a promotional tool for potential clients. A SOC 3 report could be viewed as a redacted version of a SOC 2 report – you would not obtain a SOC 3 without going through the SOC 2 audit process.
Differences Between SOC 1 and SOC 2 Reports
In the world of system and organization controls, SOC 1 and SOC 2 are two pillars that can sometimes cause confusion for businesses. While both touch upon internal controls within an establishment, the emphasis each puts is quite different. SOC 1 shines a light on the internal controls related to financial reporting (ICFR). It is a report that demonstrates the service organization’s commitment to ensuring their offerings do not adversely affect their client's financial statements.
On the flip side, SOC 2 is centered around the principles of information and data security within a cloud-based environment. When an organization completes a SOC 2 report, it sends a strong signal to stakeholders, promising that the company’s control environment is sturdy enough to handle customer information securely.
Differences Between SOC 2 and SOC 3 Reports
While a SOC 2 report plays a pivotal role in fortifying trust between a vendor and its clients, it is designed for a limited audience, primarily senior executives at the requesting entity. This report provides a deep dive into the audit methodology mapped to the Trust Services Criteria set out by the AICPA.
SOC 3, conversely, is for the masses. Designed for public consumption, these general-use reports can often be found on an organization’s website, speaking volumes about their compliance credentials. Both SOC 2 and SOC 3 undergo similar auditing procedures. The foundation for these reports lies in the five Trust Service Criteria outlined by the AICPA. It is common for SOC 2 and SOC 3 to be interlinked, as a SOC 3 report is generated based on the processes involved in a SOC 2 audit.
SOC 1 vs SOC 2 vs SOC 3 Reports
SOC 1 reports delve into an organization's internal governance related to financial reporting. In contrast, both SOC 2 and SOC 3 reports focus on the organization's adherence to one or more of the Trust Services Criteria surrounding information and data security. Notably, while SOC 2 reports are kept confidential, SOC 3 reports are public documents, serving as a testament to the efficacy of an organization's internal control mechanisms.
SOC Type 1 vs Type 2 Reports
If you are considering either SOC 1 or SOC 2 – the major contenders in the realm of SOC reporting – the subsequent decision hinges on the specific kind of SOC report you require. The choice between SOC 1 and SOC 2 signifies the category of controls you intend to review. While SOC 1 targets controls influencing financial reporting, SOC 2 zeroes in on operational and security measures. But what implications does the report type have? There are two main variations of SOC reports: Type 1 and Type 2.
What is a SOC Type 1 Report?
The SOC Type 1 report provides insights into management's portrayal of the pertinent system(s) and evaluates the appropriateness and structure of controls concerning the Trust Services Criteria at a specific moment in time.
What is a SOC Type 2 Report?
SOC Type 2 offers a more comprehensive analysis. While it encompasses all elements found in the Type 1 report, it delves deeper, showcasing the functionality of the established controls across a duration, typically spanning at least 6 months.
What is SSAE 18 (previously SSAE 16 and SAS 70)?
SSAE 18, formally known as Statement on Standards for Attestation Engagements No. 18, represents a comprehensive set of audit guidelines and standards disseminated by the American Institute of Certified Public Accountants (AICPA). This expansive standard caters to a wide range of attestation assignments, extending beyond just IT and security parameters. Historically, SAS 70 was succeeded by SSAE 16 in 2011, which later made way for SSAE 18 in 2017.
The interplay between SSAE 18 and SOC 2 might seem intricate. To make it simple, SSAE 18 stands as a versatile standard, furnishing guidelines for a variety of assurance and attestation tasks, inclusive of both SOC 1 and SOC 2 report preparations. SSAE 16, its predecessor, was tailored primarily for service organizations and pertained to SOC 1 attestations. Currently, SOC 1 conforms to the AT-C Section 320 (Delving into Controls at a Service Organization Pertinent to User Entities’ Financial Reporting Control) embedded within SSAE 18. Earlier, examinations for SOC 1 were designated as SSAE 16 evaluations. Now, they bear the SSAE 18 / SOC 1 label or are straightforwardly termed as SOC 1 assessments and inspections.
SSAE 18 lays down the procedural blueprint for executing the audit process, enveloping stages like data gathering, assessment, and documentation. Under this SSAE 18 umbrella, auditors are empowered to administer SOC 2 examinations. During a SOC 2 evaluation, auditing professionals draw from the directives outlined in SSAE 18. The SOC 2 report zeroes in on non-financial control aspects of a service organization, spotlighting areas like system security, availability, process integrity, confidentiality, and data privacy. SSAE 18 lays out the general framework for performing these audits, and the SOC 2 report uses the AICPA's Trust Services Criteria to assess the robustness of a service organization's control measures.
Compass IT Compliance Makes the SOC Reporting Process Simple
For organizations unfamiliar with the SOC reporting process or those looking to re-evaluate potential high-risk areas that might have surfaced after their previous audit, Compass IT Compliance offers the SOC Readiness Assessment. This service aids companies in pinpointing crucial internal protocols, documentation, and potential vulnerabilities within their enterprise, IT infrastructure, and security frameworks.
Undergoing SOC audits can often seem overwhelming for businesses, regardless of their scale. Our assessments are performed by skilled professionals who have extensive experience in risk and control-oriented audits and information security to validate, prior to an actual service audit, the different criteria for the 5 Trust Services Criteria defined in conjunction with an independent CPA firm. This approach ensures your preparedness and future success for this type of engagement and reduces the possibility of a qualified opinion or reporting exception. Contact us today to learn more and discuss your unique SOC reporting situation!
Contact Us
Share this
You May Also Like
These Related Stories

A Detailed History of SOC 2 Compliance

What Are the 5 Trust Services Criteria (TSC) for SOC 2?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
.webp?width=610&height=362&name=November%202023%20CTA%20(8).webp)
No Comments Yet
Let us know what you think