Social Engineering Techniques and How Yahoo Put Us All At Risk
I read this article the other day that one of my colleagues passed on to me that said 91% of all cyber-attacks begin with a phishing email. That is an incredible number and one that should grab your attention and the attention of your Sr. Leadership team. As you dig further into the statistics in the article, the top reasons for users clicking on phishing links include:
- Curiosity
- Fear
- Urgency
While fear and urgency are somewhat understandable, curiosity is the one that is mind boggling, as well as unacceptable. But, there are two distinctive paths that this can take, each with similar yet different challenges to overcome:
- The Phishing email appears to come from someone you know and trust
- The Phishing email comes from someone you don't know
Scenario # 1 is one of the most common Social Engineering techniques that attackers use to gain access to your system. They spoof an email address of someone you know, send you a bogus link to a video of baby kittens dancing in Santa outfits, and boom, you now have malware installed on your device. This is what I like to call the "go narrow" approach as it is targeted to you and preys on your trust of other people. When this email comes your way, do some investigative work to find out if the dancing kittens are legit. Send a separate email to your friend to see if they sent you the link. Call them and ask them if they sent you the link. Find out some more information before you go clicking away on links that may or may not be the dancing kittens you have been hoping for.
Scenario # 2 is the confusing one and more mind boggling of the two. Someone who you don't know sent you a random email about a random topic and you click on the link out of curiosity? Not a good idea. I like to call this the "go wide" approach. This is the equivalent of throwing you know what against the wall to see what sticks. If you send 100,000 bogus emails with Ransomware infections hidden inside and 1% of the people click on the link, that is 1,000 new Ransomware infections.
Let's take this a step further and check out the screen shot of a bogus email that I received, in my work email, that tried to get me to click on a PDF document:
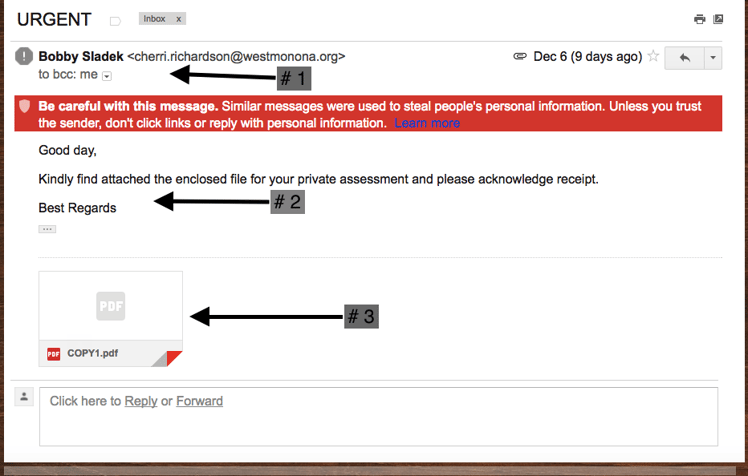
I will admit that the Google services did warn me that this email was bogus, which is good, but why they still let it through their filters is beyond me. There are 3 main points that I want to cover in this email that I received that are important, as labeled by the arrows on the picture:
- The header of the email - The email comes from "Bobby Sladek". I have no idea who Bobby Sladek is so that should be one of the first red flags. Next, Bobby's email address is bogus. It looks like this email address was stolen and is the attack vector for some form of Malware. On a side note, I don't know a Cherri Richardson either but that wouldn't have made a difference on whether I open this email or not. The final point of the header that I want to make is the fact that I am Bcc’d on the email. That is the first red flag that you are part of a larger list of people. While this isn't completely out of the ordinary, when it comes from someone you don't know with a different email address, it is trouble. I am jumping ahead a bit here into section # 2, but if this is my private assessment as indicated in the body of the email, why am I Bcc’d on it and not the primary recipient?
- The Body of the email - No salutation to me and the single sentence that makes up the body of the email has terrible structure. My QA department would have a field day with this (I know they are reviewing this post so I had to give them a quick shout out for all the work they do!). Also, there is no detail to what this "private assessment" is. Seems phishy to me (see what I did there?)
- The attachment - No preview and a basic name of COPY1.pdf doesn't sound legit to me. In fact, it sounds like a nightmare wrapped in a PDF document
So here is the big question: Did I click on the attachment? NO! All the curiosity in the world couldn't get me to click on my private assessment that I never took. But you know what, I bet many people did click on the attachment and that is the shame of it.
By now you have read 807 words and are wondering why you should care. Here's why: Yahoo. Yahoo announced that they have uncovered a second, separate attack that compromised the accounts of 1 Billion users. Yes, that is Billion with a capital B. As I just mentioned, that is separate from the 500 million user breach they announced in September. I am not a math major but that brings the total of compromised accounts to 1,500,000,000. When you consider that the entire population of the world is 7,400,000,000, that translates to 20% of the ENTIRE WORLD'S POPULATION had their accounts compromised. Awesome job Yahoo! Here are a couple of tips for you Yahoo account holders:
- Delete your Yahoo account. Now.
- If you used the same password on your Yahoo account for other accounts, change those immediately (and don't reuse passwords across sites).
With 1 Billion new users accounts out in the wild and in the hands of individuals and organizations that have less than honorable intentions, it is critical that you prepare your staff for the threats they could be facing soon!
Contact Us
Share this
You May Also Like
These Related Stories
Phishing Examples: Google Docs Scam

Social Engineering Techniques, the Stealth Bomber, and You!

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think