The NIST Cybersecurity Framework - The Identify Function
Last week we provided a very high-level overview of the NIST Cybersecurity Framework, the core (5 functions) of the framework, and the categories within each function. This week, as promised, we are going to dig into the first function of the framework – Identify. If you recall from last week’s post, the purpose of the Identify function is to, “Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.” This is the stage where you evaluate the context of your business, what systems you have to support your critical business activities, what cybersecurity risks are present in the threat landscape today and how you can prioritize your efforts and strategies to mitigate your overall risk. One key point to note is that the NIST Cybersecurity Framework is constantly growing and evolving, it is not a stagnant exercise that you do once and forget about. Threats change, systems change, and people change so you need to constantly be identifying the risks present to your organization.
In the Identify function of the framework, NIST breaks the overall function into 5 categories, which we are going to dig into a bit in a moment. Another key point to make is that these 5 categories within the Identify function are then further broken down into subcategories. However, for purposes of these blog posts, we are only going to discuss the categories within the Identify function. Here is a brief description of the 5 categories contained in the Identify function with the definition straight from NIST and then a description in layman’s terms:
- Asset Management (ID.AM) – “The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to business objectives and the organization’s risk management strategy”. What I find important about this category is that it is not just related to hardware and software systems. Instead, this is looking at the entire picture to include hardware and software, but also at people and facilities. People are always your weakest link in Information Security so it is important to evaluate the people you have in critical positions and when turnover happens.
- Business Environment (ID.BE) – “The organization’s mission, objectives, stakeholders and activities are understood and prioritized; this information is used to inform cybersecurity roles, responsibilities, and risk management decisions”. While I think that business environment seems all encompassing, the one word that comes to mind in this category is communication. The NIST Cybersecurity Framework encourages that all levels of the organization have buy-in when it comes to Information Security, as evidenced by the importance on this specific category.
- Governance (ID.GV) – “The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk”. In a nutshell, this category talks about what your responsibilities are as an organization based on your business and what impact that could have on Cybersecurity. Again, communication is key!
- Risk Assessment (ID.RA) – “The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals”. I could talk for another 5,000 words on this topic alone, but I won’t (you’re welcome!). The key point I want to make is that this falls under the Identify category, not the Protect category or any other category. To identify your risks, you need to assess your risks. Of course, to protect your organization you need to assess your risks, but it makes sense to identify before you protect, doesn’t it? Otherwise, how do you truly know you are protecting the right thing? You don’t because you are probably guessing which is why the Risk Assessment is so critical in the Identify function of the framework!
- Risk Management Strategy (ID.RM) – “The organization’s priorities, constraints, risk tolerances, and assumptions are established and used to support operational decisions”. I really don’t need to add anything here because it is self-explanatory. How can you develop a risk management strategy without knowing your risks? You can’t and therefore you shouldn’t.
The final key point that I want to make around these categories has to do with the order in which they are conducted. This is very important as when you look at these categories, each one logically builds on the next one. If you look at it like a simplified flow chart, it would look a bit like this:
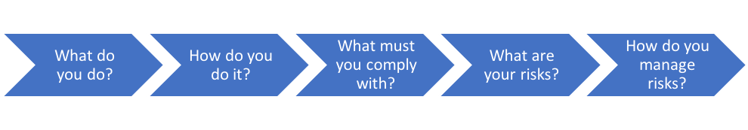
Those simplified items above match well to the 5 categories within the Identify function. The question is where do you begin? The first thing that you really need to look at in the Identify function, and the entire NIST Cybersecurity Framework, is getting your IT Security Policies and Procedures created and up to date. This can be a very difficult task; however, it is critical for the NIST Cybersecurity Framework. Next week we will cover the next function of the framework, Protect! Until next week...
Contact Us
Share this
You May Also Like
These Related Stories

What is the NIST Cybersecurity Framework?

The NIST Cybersecurity Framework Functions - Protect

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think