Macs Can Get Viruses?
by Jesse Roberts on August 21, 2019 at 2:15 PM
Through my work at Compass IT Compliance I was recently contacted to deal with an issue regarding a Mac computer acting suspiciously. What does suspicious mean? In the case of this particular Mac, whenever a user tried to open the Safari web browser they were getting directed to the h …
The Importance of Testing Your Business Continuity Plan
by CJ Hurd on July 3, 2019 at 1:00 PM
Alright boys and girls, time to put your pencils down – we are taking a TEST! These may have been some of the scariest words you have ever had to hear. Personally, I will be thrilled if I never have to take another test and I know very few people who look forward to doing so.
Response Operations: BCP, IRP, and DRP - Why You Need all Three
by Andrew Paull on February 21, 2019 at 1:00 PM
No well-managed organization is immune to the risk of the potential business interruptions that may occur from time to time, whether caused by acts of nature, malicious attack, or simple human error. Depending on the severity of the interruption and the organizational assets and busin …
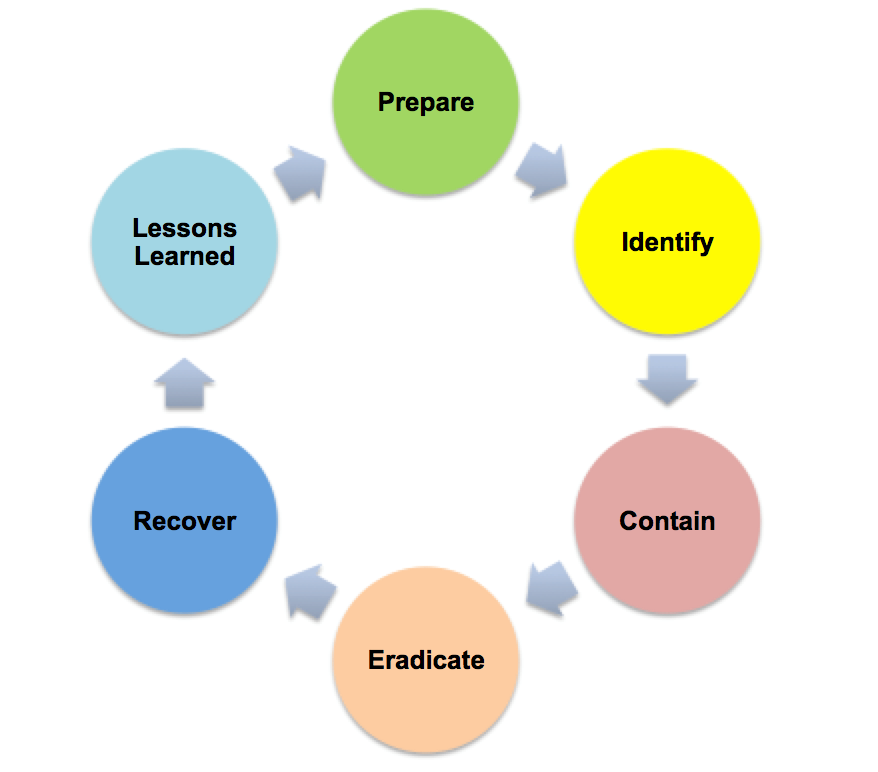
Why You Need an Incident Response Plan....Now!
by TJ Quirk on March 21, 2017 at 10:00 AM
You’ve been breached. Now what? New vulnerabilities are coming fast and furious. The unfortunate truth for most of us is, it’s not a matter of IF we are breached, it’s a matter of WHEN we are breached. Replace the worry with a plan - an Incident Response Plan. What qualifies as an inc …
Why You Need an Incident Response Plan Now!
by Geoff Yeagley on June 7, 2016 at 10:43 AM
Two weeks ago, Compass IT Compliance had the opportunity to attend and present at the Card Not Present Conference in Orlando. This conference focuses on working with organizations that accept credit and debit cards either online, over the phone, or any other way where the credit or de …
Critical Security Control 19: The Incident Response Plan
by Geoff Yeagley on May 17, 2016 at 12:16 PM
In the world of Information Security, we have all heard of the Center for Internet Security Top 20 Critical Security Controls (CSC's) which is formerly known as the SANS Top 20. This is a list of the 20 IT Security Controls that an organization can implement to strengthen their IT Sec …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)