What is My Password? How About a Passphrase Instead?
by Ron Scarborough on January 4, 2018 at 9:15 AM
Recently I met with a doctor who had as much paper with fancy lettering framed on their wall as anyone person could want. With all that impressive education looking down upon me, I watched as the doctor fumbled through password attempt after password attempt until ultimately and predi …
Ransomware Examples - Locky is Back and Worse Than Ever!
by Geoff Yeagley on October 5, 2017 at 9:48 AM
For a period of about 18 months, Ransomware dominated the news related to information security. Companies of all sizes and verticals were under attack by cybercriminals that were looking to make a quick buck, or a lot of bucks in some cases. Then, all of the sudden, Ransomware sort of …
Urgent Alert - New Spear Phishing Attack
by Geoff Yeagley on August 15, 2017 at 11:10 AM
It has come to our attention that cyber criminals have begun exploiting a vulnerability within Microsoft PowerPoint’s Object Linking and Embedding (OLE) interface to evade antivirus detection in an attempt to silently install malware applications on Windows based computer systems.
Another Day, Another Major Ransomware Outbreak...
by Geoff Yeagley on June 28, 2017 at 5:00 PM
A little over a month ago, a strain of Ransomware called WannaCry made headlines due to the incredibly successful nature of the attack as it infected hundreds of thousands of users around the world. This ransomware was delivered through an unpatched vulnerability in the Microsoft Oper …
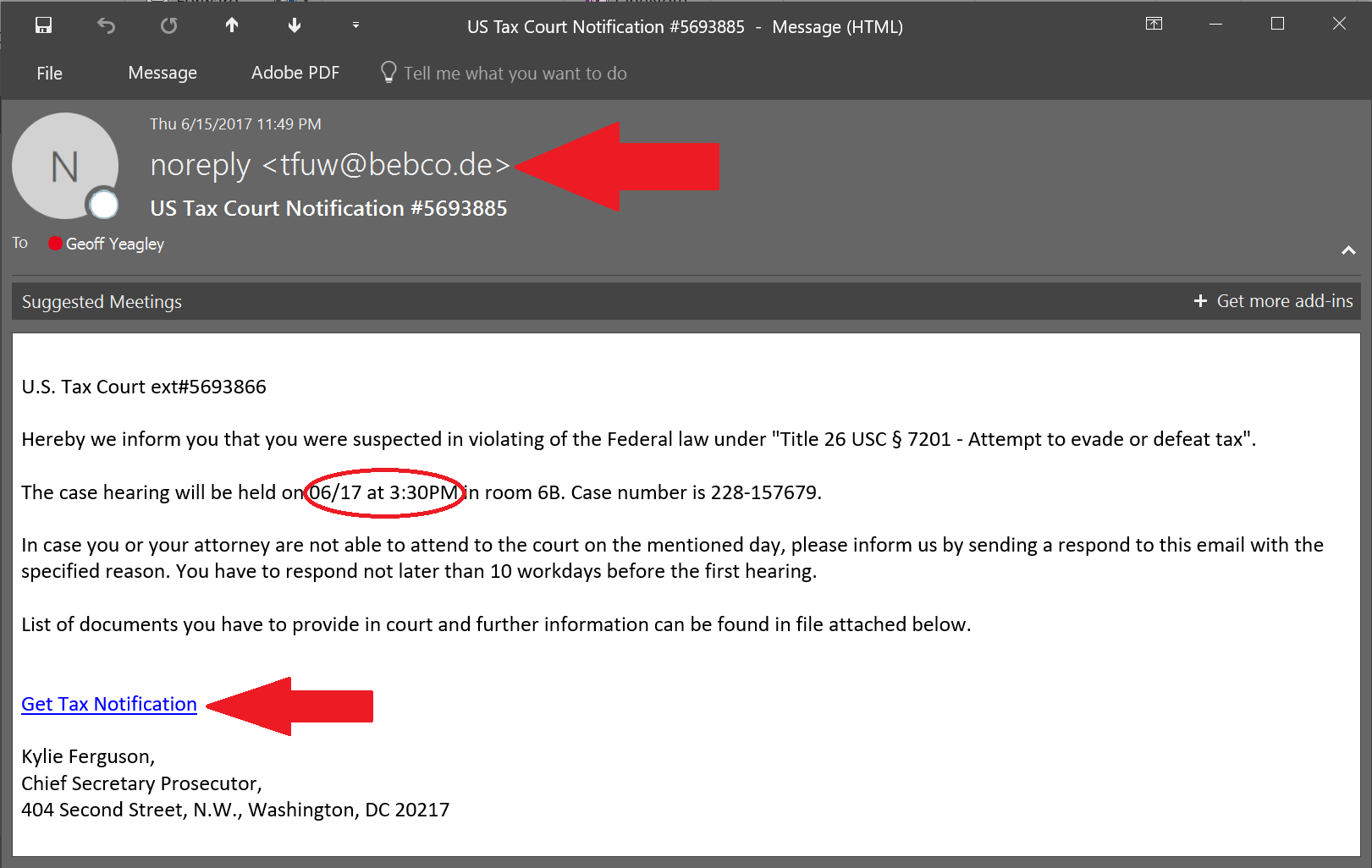
Phishing Examples: Even the Security Folks Get Targeted... Again!
by Geoff Yeagley on June 23, 2017 at 10:51 AM
If you have been reading the blog for a while, you know that I take phishing examples that I receive or my co-workers receive, post them to the blog, and point out the things that you need to be careful of. I do this primarily to educate folks about what the latest threats look like, …
The NIST Cybersecurity Framework - The Identify Function
by Geoff Yeagley on June 21, 2017 at 10:19 AM
Last week we provided a very high-level overview of the NIST Cybersecurity Framework, the core (5 functions) of the framework, and the categories within each function.
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)