Why Your Staff Needs Security Awareness Training Now!
by Geoff Yeagley on August 24, 2016 at 11:15 AM
We have all been there. We are sitting at our desks, doing our work and the email pops up. Usually from our IT Department or our boss, the email tells us that we need to complete our annual Security Awareness Training within the next 2 weeks. What's the first thought that goes through …
Phishing - Even the Security Folks get Targeted Part II
by Geoff Yeagley on April 7, 2016 at 9:30 AM
Phishing schemes come in all different forms, shapes, and sizes. Hackers and thieves are smart and they will do whatever they think they can do to get access to your sensitive information. Some of these methods include emails, social media "like farming", pre-text calling, etc. The co …
Phishing Emails, Ransomware, and the Government
by Geoff Yeagley on April 5, 2016 at 10:00 AM
Every day that you turn on the news, there is another story or article about a Ransomware attack that has taken place. Most recently, these stories are focused around healthcare organizations where significant ransoms have been demanded. What we haven't heard much about, but is just a …
How Phishing Emails Can Cost You $40,000
by Geoff Yeagley on March 22, 2016 at 10:00 AM
To me, math is what makes the world work. If you think about it, just about everything involves math, especially when it comes to business. When I was going through my MBA program, I really underestimated the amount of math and calculations that you needed to perform for essentially e …
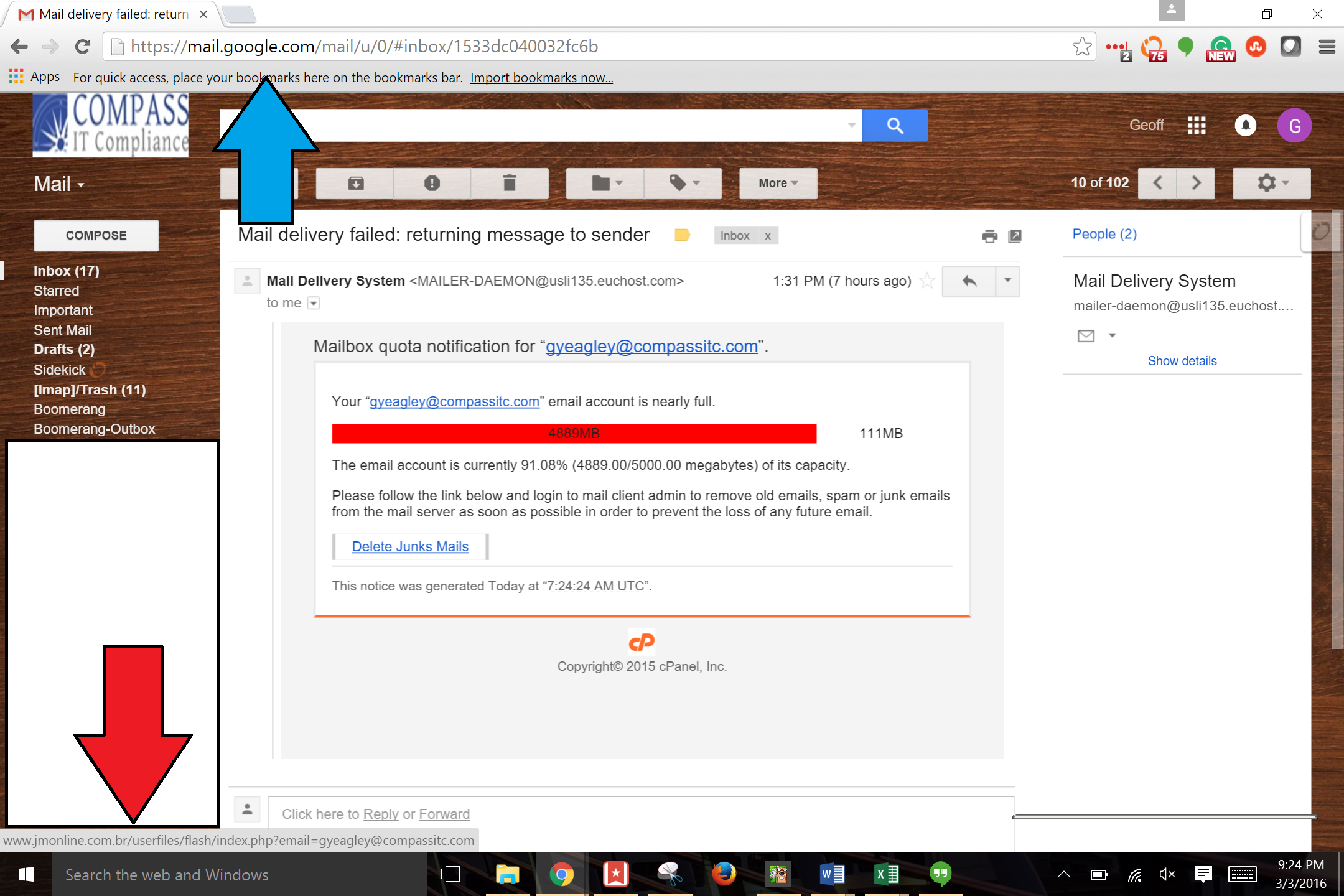
Phishing Examples: Even the Security Folks Get Targeted
by Geoff Yeagley on March 4, 2016 at 10:00 AM
We all hear about phishing emails. All the time. In fact, there is a never ending dialogue about phishing emails in the news, the most recent one being the IRS emailing to say that you owe them money and they are going to arrest you if you don't pay immediately. As a side note, this i …
IT Risk Assessment and the SANS Top 20 - Part IV
by Geoff Yeagley on February 23, 2016 at 11:00 AM
I know, I know. Before you even say it, they are called the Center for Internet Security Critical Security Controls, not the SANS Top 20 anymore. But, everyone knows them as the SANS Top 20 and often times still refers to them by this name which is why I stuck with it for the final pa …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)