3 Reasons Why You Need a HIPAA Risk Assessment Right Now
by Geoff Yeagley on June 16, 2016 at 10:31 AM
HIPAA is in the news all the time. Whether it is the tragedy that struck Orlando last weekend, the news of the HIPAA Audits coming, or a new healthcare breach being reported, we are constantly bombarded with why HIPAA compliance is critical. As with any organization, protecting and sa …
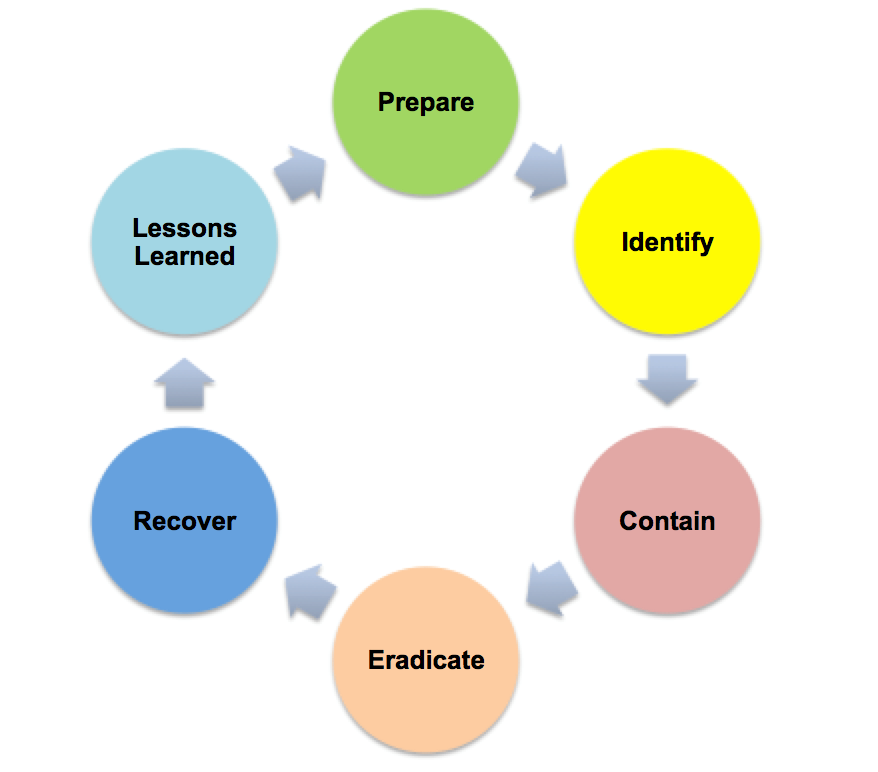
Critical Security Control 19: The Incident Response Plan
by Geoff Yeagley on May 17, 2016 at 12:16 PM
In the world of Information Security, we have all heard of the Center for Internet Security Top 20 Critical Security Controls (CSC's) which is formerly known as the SANS Top 20. This is a list of the 20 IT Security Controls that an organization can implement to strengthen their IT Sec …
Ransomware Alert: Big Business and the Evolution of Phising
by Geoff Yeagley on May 3, 2016 at 1:20 PM
Ransomware is certainly nothing new as it has been around for several years, however, it sure is gaining quite a bit of attention these days. In fact, Ransomware is gaining so much attention that on Friday, the FBI released an article discussing the fact that ransomware is on the rise …
How Phishing Emails Can Cost You $40,000
by Geoff Yeagley on March 22, 2016 at 10:00 AM
To me, math is what makes the world work. If you think about it, just about everything involves math, especially when it comes to business. When I was going through my MBA program, I really underestimated the amount of math and calculations that you needed to perform for essentially e …
The HIPAA Risk Assessment - Who Needs One and When?
by Geoff Yeagley on March 9, 2016 at 10:30 AM
Healthcare breaches are nothing new, in fact they have become quite common in the news on a weekly basis. As an example of this, a Central Florida Oncology provider recently announced that it suffered a data breach at the hands of a hacker, resulting in the compromise of the personal …
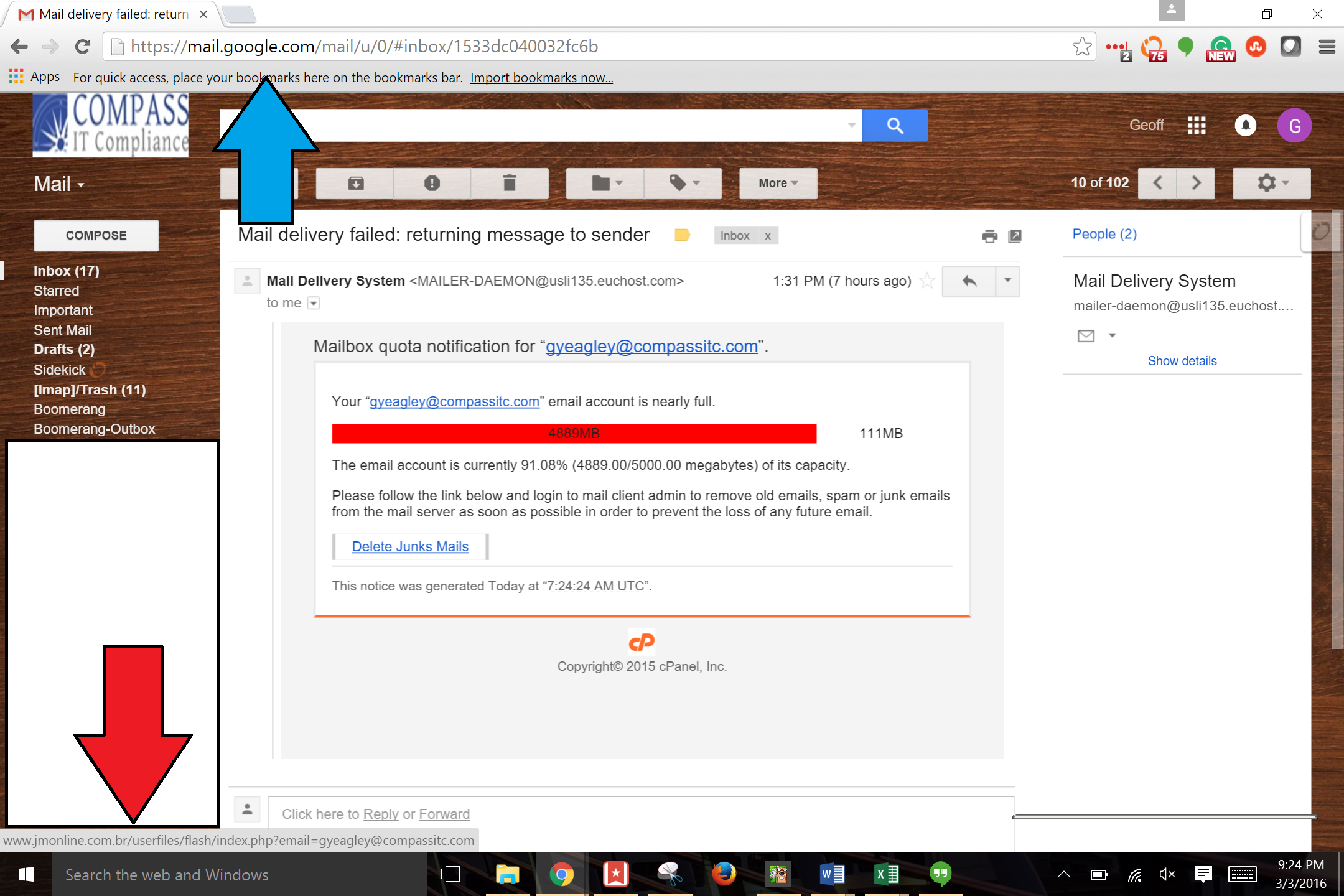
Phishing Examples: Even the Security Folks Get Targeted
by Geoff Yeagley on March 4, 2016 at 10:00 AM
We all hear about phishing emails. All the time. In fact, there is a never ending dialogue about phishing emails in the news, the most recent one being the IRS emailing to say that you owe them money and they are going to arrest you if you don't pay immediately. As a side note, this i …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)