QRishing – A New Version of an Old Scam
by Jake Dwares on November 17, 2021 at 3:00 PM
QR codes are everywhere these days. Codes can be found on restaurant menus (since the start of COVID), company websites, business cards, flyers, brochures, etc. Most individuals are likely to have seen one or scanned one at some point recently.
Combating Cognitive Bias to Mitigate Social Engineering Attacks
by Peter Fellini on April 9, 2021 at 1:00 PM
“When dealing with people, remember you are not dealing with creatures of logic, but with creatures bristling with prejudice and motivated by pride and vanity” – Dale Carnegie In this quote, American writer and lecturer Dale Carnegie touches upon the topic of cognitive bias.
The Online Shopping Scam That Almost Duped a Security Professional
by Andrew Paull on December 10, 2020 at 3:15 PM
A great many things have changed in our daily lives since the COVID-19 pandemic began rampaging across the world at the beginning of this year. We have been collectively forced to adapt to working from home, schooling from home, shopping from home, and even receiving healthcare from h …
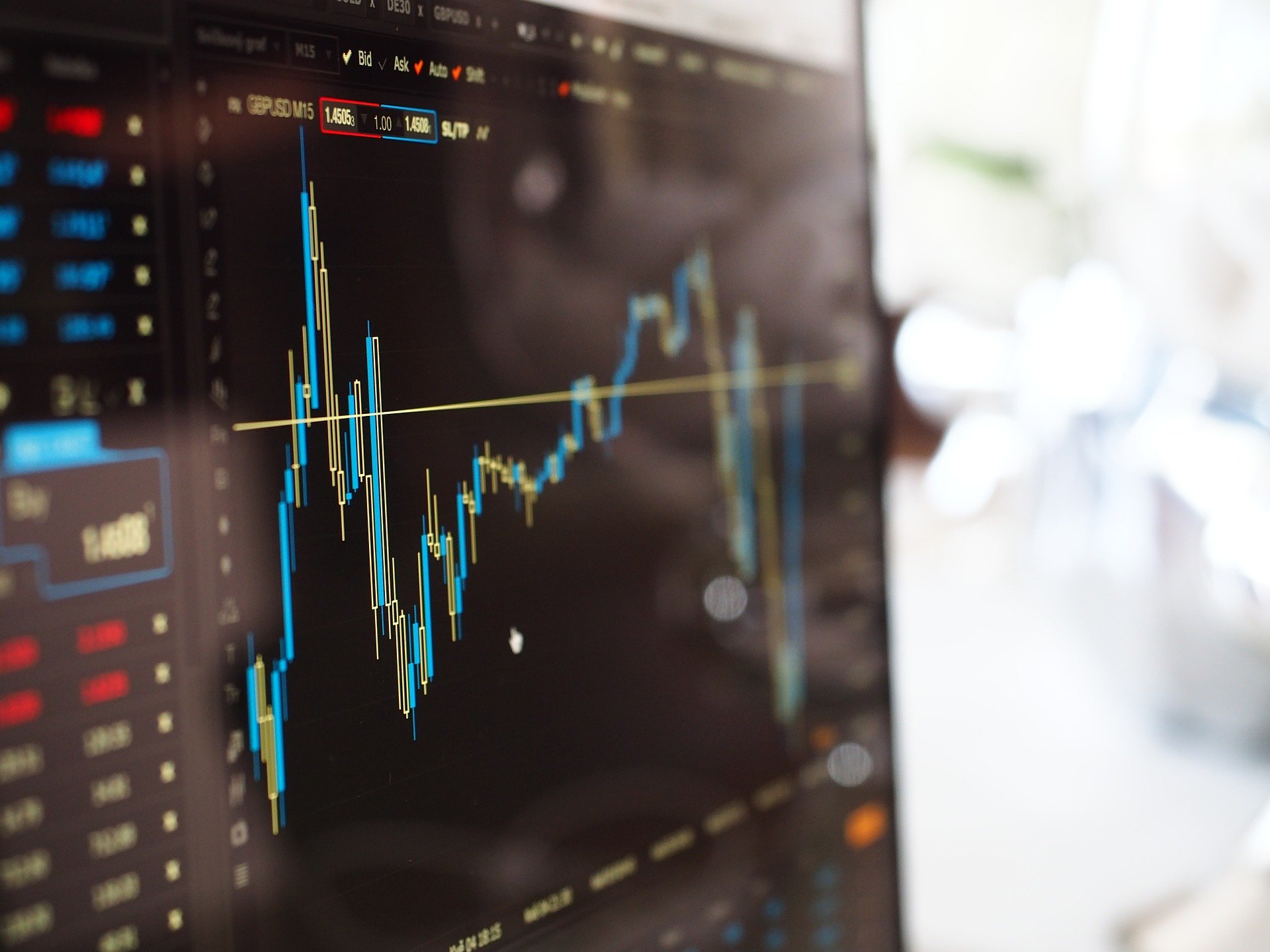
So You Started Trading Stocks – Is Your Account Secure?
by Peter Fellini on December 3, 2020 at 1:00 PM
The COVID-19 pandemic has had a significant effect on all of us, with many individuals now working from home, furloughed, or losing their jobs permanently. This had led to a sharp increase in personal stock trading. Some are doing it to supplement their income, while others are hoping …
VA Data Breach Exposes the Personal Info of 46,000 Veterans
by CJ Hurd on September 24, 2020 at 1:00 PM
Being hacked is unfortunately still an all too common occurrence. Even as security measures get stronger, reports of breaches and compromises of individual’s personal information do not seem to be slowing down.
Situational Awareness – How Strong Are Your Spidey Senses?
by Peter Fellini on September 17, 2020 at 3:15 PM
How aware are we of our surroundings? What is happening around us that we are not aware of? Being more cognitive of our surroundings at work and at home can bring a lot of positive results to our corporate security posture.
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)