Helping a Social Engineer Achieve Their Goal
by Peter Fellini on May 15, 2019 at 1:00 PM
I know the title of this blog post seems a little weird. Why would we help a social engineer achieve their goal? Well, we might not want to, but we all do it in some way and some people are more guilty of it than others.
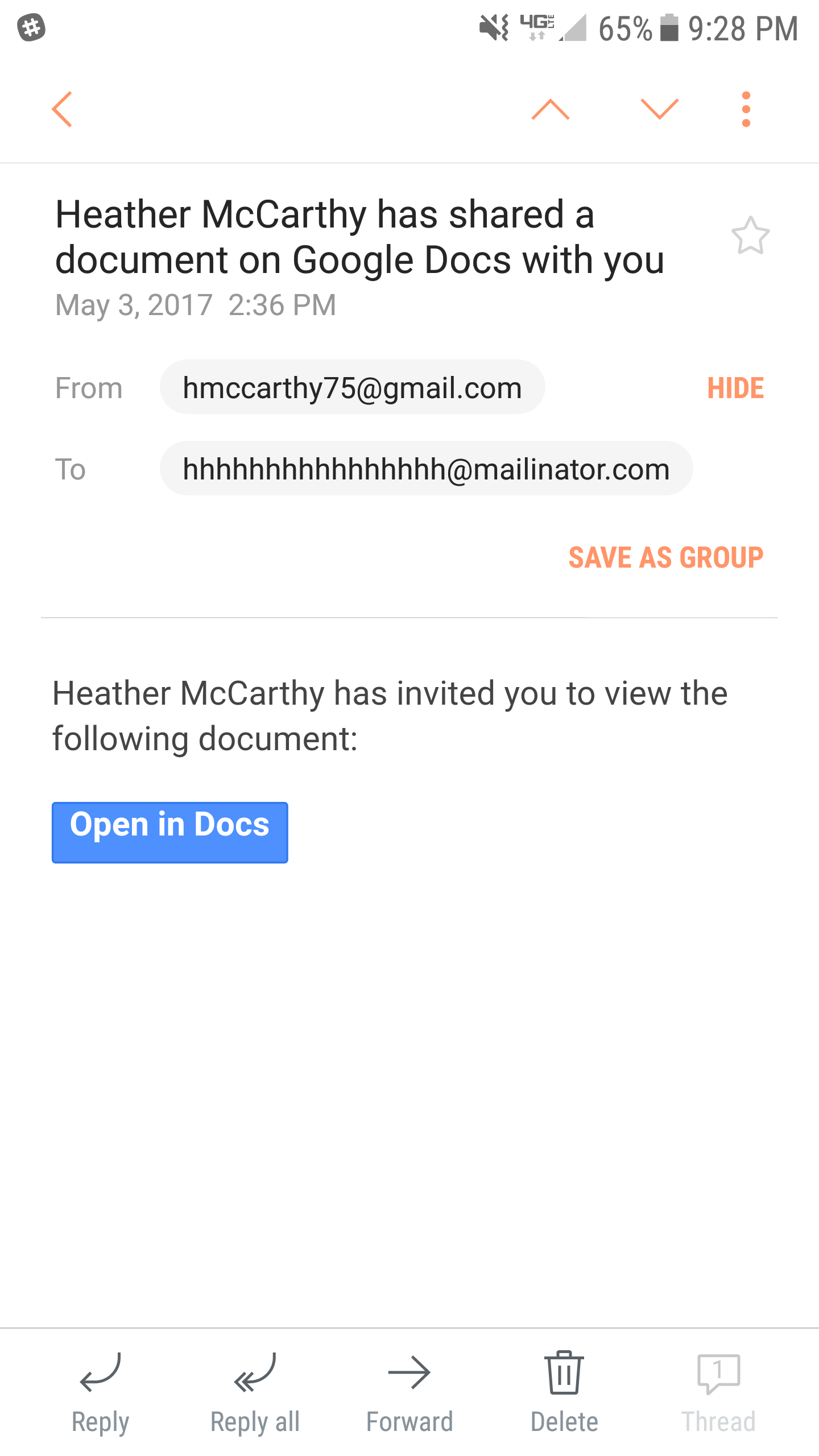
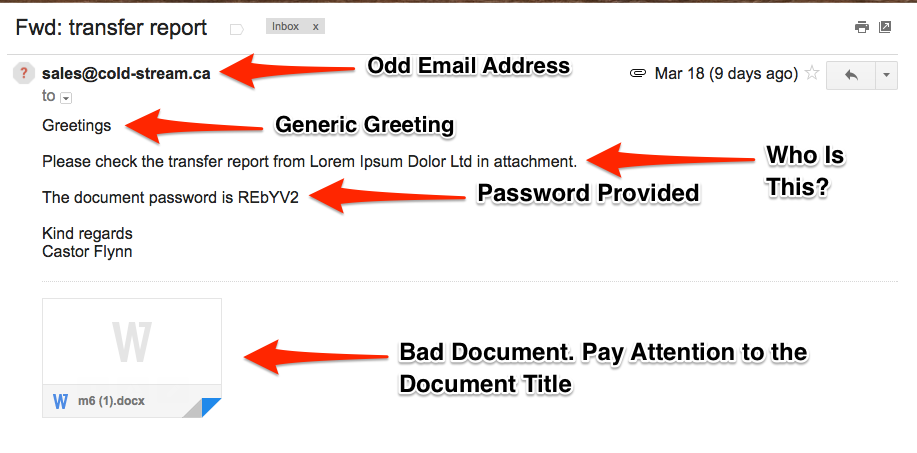
Phishing Examples: Google Docs Scam
by Josh McDonald on May 4, 2017 at 2:16 PM
Friends of Compass, On this blog, phishing examples are nothing new. But, it is our job to share this information with you so that you stay alert, know what the threats are, and what you can do in the event you fall victim to an attack. You may have seen the recent reports of a Phishi …
Social Engineering Techniques, the Stealth Bomber, and You!
by Geoff Yeagley on May 2, 2017 at 9:45 AM
We write a lot on this blog about the different Social Engineering Techniques that are being used by bad actors today. We do this to educate you on the threats that are out there and the methods that these organizations will use to achieve their main goal: Steal sensitive information …
What is Social Engineering? Part III
by Derek Morris on April 11, 2017 at 10:00 AM
What is Social Engineering? In this blog, I would like to shed some light on some other types of social engineering and provide some context on how to protect your business and self. In my first two blogs, I jumped into the Phishing and Spear Phishing pieces of a social engineering at …
What is Social Engineering? The Phishing Email
by Derek Morris on April 4, 2017 at 9:30 AM
What is Social Engineering? Part 2 The seemingly most common way for an attacker to use social engineering to gain entry, exfiltrate information or disrupt business is through email phishing. As I mentioned in the previous blog, slick tactics like using nicknames and shockingly proper …
What is Social Engineering? Part I
by Derek Morris on March 14, 2017 at 9:45 AM
This post will be the first part in a series of three blog posts that outlines some of the most common methods “hackers” use, from a very high level, to gain access to your systems though social engineering tactics. The next two posts will dig a bit deeper into the different methods, …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)