When I’m tasked with creating phishing emails for clients, I begin by looking up what the recent phishing trends are in the real world, or the top 10 most reported phishing attacks for the month / year. I often end up finding scams about winning the latest iPhone from a phone service provider or winning a free trip to a concert / destination of your choice if you fill out a form. Phishing emails will also utilize intimidation tactics, such as an IRS tax fraud email or an alert that your banking account needs immediate action. You may think that that’s all attackers can use against you, but it goes deeper than that.
If the attacker was really out to get your sensitive information, they could look you or your coworkers up on Facebook, Twitter, Google, or Instagram to see what your interests are, where you work, who your family and friends are, etc. They’ll then leverage that information in some way to get you to believe that the email they sent you isn’t a scam. It’s always best practice to lock down your social media profiles to only your friends and family.
Through my experience I’ve found that many users are compromised by clicking on emails such as the ones I mentioned above. I believe emails such as these still get clicks because people are simply not being properly trained on how to identify a phishing attack from a legitimate email. A phishing email will typical carry small clues to its fraudulent identity, such as improper grammar. I will show you an example of a phishing email and how you can properly train yourself to recognize such an attack. Here is an “Amazon order receipt” email I received:
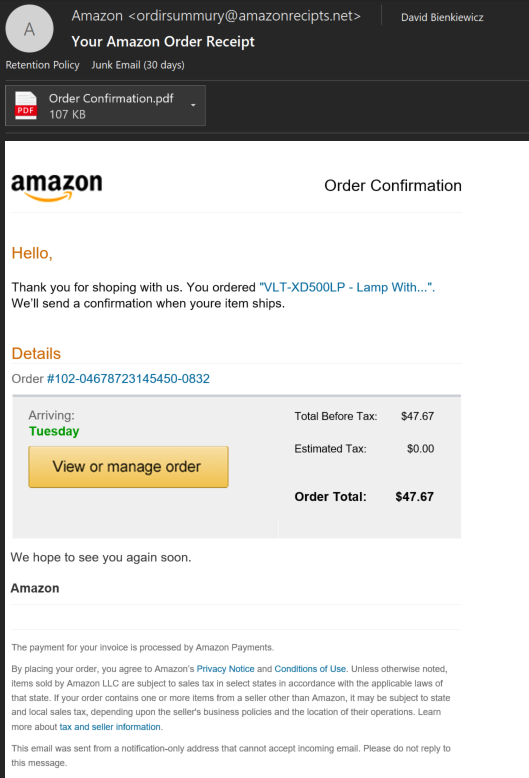
First let’s look at the sender’s email address. There are a couple of questions you should ask yourself about the sender. These questions include:
- Should I be receiving this email?
- Is this the email address I should get notifications to from this company?
- Is the sender email address spelled correctly?
Right away, this phishing email fails all three questions. I didn’t order this item, so I should not be getting this email. My email address it was sent to is not linked to an Amazon account. And the sender email address is not legitimate. While these clues were obvious in this scenario, a very targeted attack could pass some or all of these questions.
Next, let’s look at the email itself. Before clicking on anything in the email, always read the email first. As you can see in this example the attacker has made many grammatical mistakes. This is often the result of phishing attempts originating from foreign countries. Here’s another set of questions you should ask yourself when examining the body of an email:
- If it’s coming from a retailer or company, shouldn’t the spelling & grammar be correct?
- Have they addressed me with any identifiable information, or referred to me in general terms such as “sir” and “madam”?
- Is the email asking me to click a link, download an attachment, or provide any type of information?
In most cases, actual emails from companies you subscribe to will have few to no grammatical errors. Also, many phishing emails have little information on you besides your email address, so they won’t be able to address you by your name. However, in this case they did know my name. And finally, for the phishing email to be a success, it will need to have you complete some sort of task. This can include opening and downloading a malicious attachment, clicking a link to a harmful website, or getting you to respond with information that they will then use against you or others. While it may not seem like the example I’ve shown is asking me to complete a task, its purpose is to make me curious enough about this order I didn’t make that I’d be tempted to click the links in the email. After clicking, I’d likely be prompted to enter my Amazon credentials. And after that they’ve succeeded, and my account is compromised. Again, a very targeted phishing email may contain no grammatical errors and have your true name listed.
Always make sure to closely examine the links in an email. To do this, simply hover over the link the sender wants you to click and you will see a website URL. Hovering to see the true link is important, as it is very easy to type out a link, but have it redirect you somewhere else. If the true link doesn’t look properly structured and spelled, like “payments-amazon.com” or “amazonrecipts.net” instead of “amazon.com”, you should immediately flag the email.
Always remember, if you're unsure of the legitimacy of the email, don’t click or open anything. Report any phishing email to your IT Administrator immediately. Compass IT Compliance is an industry leader in phishing assessments and security training. We’ve partnered with organizations across the country to train employees and test them with simulated phishing attempts. Contact us today to learn how you can prepare your workforce to recognize these cyber-threats!
Contact Us
Share this
You May Also Like
These Related Stories

Spear Phishing: Targeted Attacks with Higher Success Rates

Phishing vs. Pharming: What's the Difference?
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think