This post will be the first part in a series of three blog posts that outlines some of the most common methods “hackers” use, from a very high level, to gain access to your systems though social engineering tactics. The next two posts will dig a bit deeper into the different methods, what they look like, and how you can recognize them if they happen to you.
What is Social Engineering? Merriam Webster’s definition of Social Engineering is, “the management of human beings in accordance with their place and function in society”. I humbly find this definition not quite dialed in. Recently, I read “The Art of Deception” by Kevin Mitnick and in that book, he clarifies what social engineering is and how it’s used to deceptively accomplish a certain task, goal, or get sensitive data. People, at some time in their lives, may be socially engineered by another person. There could be malicious intent involved. The malicious intent may be part of information gathering to gain access into your company or personal information. As humans we have this trait to find commonality with others which is what opens us up to being social engineered.
When we think about the question “What is Social Engineering?”, there are two methods that are the most common:
The phone is commonly used to manipulate people into giving out information verbally. If one is not aware of what can or can’t be given out, this can lead to a leak of information by the person representing the organization. Pressure or urgency when talking with someone tends to make the situation tenser and creates a level of discomfort. The person being engineered may just do what the person is asking to end the situation. In other cases, impersonation is used to make the target “do” something or give out information. People tend to adhere to the hierarchy of management, so pretending to be the manager of a particular department may be a useful tactic.
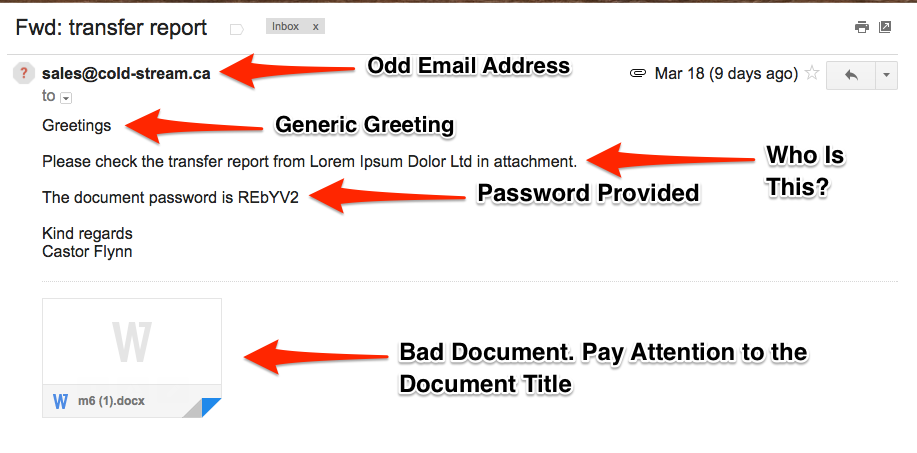
Emails are another manner used to socially engineer a target. Phishing emails are an example of social engineering at work. Details in the email create the deception necessary to have the target click or open a part of the email. In some cases, emails have a sense of urgency, creating a familiarity by mentioning names, nicknames, or recent events to make the social engineering much more effective.
This video shows a “hacker” in the act of social engineering someone to get information she wanted. https://www.youtube.com/watch?v=lc7scxvKQOo
I recently investigated a social engineering attempt via email. The email was crafted directly to an executive with the use of his nickname, perfect spelling and grammar, and mentioned the person in charge of the financial processes by her nickname as well. Just to add one more topping to this sundae, the email had the “Sent from my iPhone” below the signature. The basis of the email was to have money wired to a certain fake company. Situational awareness and security awareness training prevented this bogus email from succeeding.
Education is the best defense against social engineering attempts on the phone or email. Knowing what to look for when verifying the source of a phone call or email, as well as identifying where a link may send you before clicking on it. Having defined policies around what information is deemed private/sensitive/confidential is a starting point for this defense. Finally, there are certain times where your gut may tell you “something isn’t right here” ….trust it! In many situations in life, trusting your gut may be the best defense. If it doesn’t seem right, it usually isn’t!
These Related Stories


No Comments Yet
Let us know what you think