Two weeks ago, Compass IT Compliance had the opportunity to attend and present at the Card Not Present Conference in Orlando. This conference focuses on working with organizations that accept credit and debit cards either online, over the phone, or any other way where the credit or debit card is not physically present to a representative of the merchant, hence the name Card Not Present. Without a doubt, the biggest item that was discussed throughout the conference was the need for organizations to have an Incident Response Plan in place. In this blog post, we are going to talk about what an Incident Response Plan is and what the 6 key steps to an effective plan are.
So what is an Incident Response Plan? As a definition, an Incident Response Plan is a detailed, organized plan that anticipates various threats, creates a team made up of cross-functional roles throughout the organization with the goal of addressing and managing the aftermath of a security breach or attack that limits damage and reduces recovery time and costs. In a way, you could sort of think of an Incident Response Plan as a Business Continuity Plan specific to IT Security incidents and breaches. It is a playbook so key members of the organization know exactly what they need to do and when they need to do it to minimize damage, downtime, and contain costs. The key point in this is that this is an organizational effort, not just and Information Technology effort.
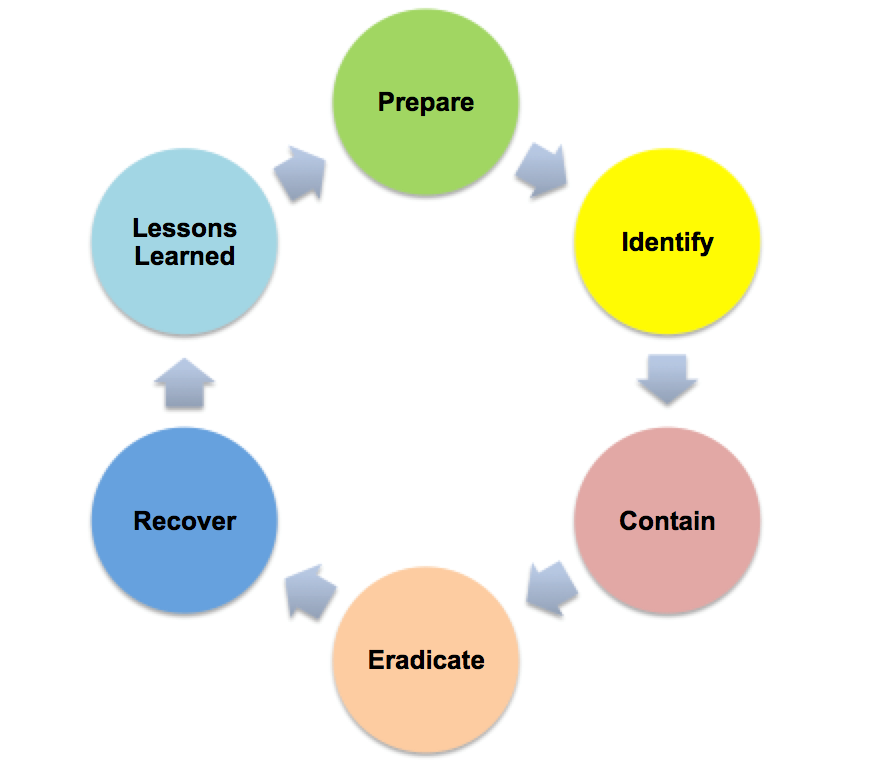
A good Incident Response Plan has 6 key "steps" that we will outline and provide a brief overview of below:
1.) Prepare
While all steps are crucial, preparation is one of the most important. You can't respond effectively to something that you didn't prepare for. In this step, you are creating the foundational policy around responding to an incident, educating your staff on what an incident is, and identifying critical systems and targets
2.) Identify
This step is exactly as it is called. Identifying incidents and what processes you have in place to quickly and correctly identify these incidents. Some of these processes might include system log events, automated notifications, and internal testing activities
3.) Contain
After you identify an incident, this step deals with containing the incident as quickly as possible to minimize damage. You would assess the impact of the incident and then determine what the appropriate next steps for containment might be, such as quarantining a system, shutting a system down, or tolerating the incident based on level of risk
4.) Eradicate
Investigate the origin and remediate the root cause. While this sounds simple, the key here is finding the root cause. Time is of the essence and you need to find what the root cause is and remediate appropriately
5.) Recover
This is the step where you restore your data, verify that your remediation strategies worked as anticipated, and monitor for any signs of recurrence or weakness
6.) After Actions Review (AAR)
I said that the Prepare step was the most important. This is the second most important (again, they are all important). This step covers what happened, what was supposed to happen, and lessons learned for next time
The Incident Response Plan should not be something that you create, put in a fancy binder on a shelf, and give it to auditors / examiners when they come to your organization. Like a true Business Continuity Plan, you must continually test your plan and update your plan accordingly. For all intensive purposes, it is a living and breathing document that should be a significant part of your organizations risk management strategy.
In closing, I will leave you with a quote from my email signature that I think is absolutely perfect for this blog post by the great Benjamin Franklin:
"Fail to prepare, prepare to fail"
These Related Stories

No Comments Yet
Let us know what you think